Selçuk J. Appl. Math. Selçuk Journal of Special Issue. pp. 117-130, 2011 Applied Mathematics
Smart Card Approach for Secure Data Communication Tarık Yılmaz
Selçuk University, Ilgın Vocational School Of Higher Education , Konya, Turkiye e-mail: tyilm az@ selcuk.edu.tr
Abstract. With the introduction of internet technology, e-trade, voice and video transfer and social networks are increasingly becoming widespread. Thanks to these technologies, people can do their jobs in a virtual environment non-spatially and rapidly. However, the security of the data people share using these technologies is serious concern. In this study, a method to provide secu-rity of the data shared on the internet is proposed. This method is developed by integrating smart card technology and encryption techniques. In the appli-cation section, method and the software developed to operate the method are defined in details.
With the application developed, secure data encryption was realized, which is the aim of the study. It was found out that it can be used in various fields from the security of computers and files in local networks to on-line messaging and e-trade.
Key words: Smart Card, Encryption and Decryption Algorithms, Secure Data Communication.
2000 Mathematics Subject Classification: 14G50. 1. Introduction
Security is an indispensible component in data communication environments. The proliferation of data sharing from a small computer network to world-wide web has brought along a set of security problems. The main reason for this is that even local computer networks are open systems and data that travels on it is vulnerable to seizure. In particular, data packages send on the internet goes through many networks open to public, which makes these packages accessible. This turns into a serious concern when top secret information is transferred on the internet. The internet will never be a secure place for doing job and for secret or personnel correspondences unless this kind of information is protected [2]. Information security is achieved by elimination of thread of being listened to by others, amendment of information and identity forgery and the primary tool used for this purpose is cryptography.
Cryptography is branch of science which studies information security and in-cludes the conversion of information from a readable state to apparent nonsense
[8]. Cryptography enciphers information (e-mail, message, any file on the disc ect.) making it nonsense to unauthorized people and thus protects its secrecy. Cryptography is basically concerned with the following issues [1]:
a) Secrecy: Information is not to be readable to unauthorized people. b) Integrity: Information is not to be changed while they are being transferred.
c) Undeniability: Person who sent the information is not to be eligible to deny that s/he sent the information.
d) Identity determination: Sender and receiver can identify each other’s identities. Any unwanted guest is not to be able play the role of sender or receiver.
In computer networks and on the internet, provision of basic components of security like data secrecy, identity confirmation and recognition and the protec-tion of data integrity is desirable. But there are some handicaps in cryptography which is related to the proper protection of the cipher keys by the users [16]. This security is violated deliberately or unintended. This violation tarnishes information security [3]. Hiding cipher keys from the users themselves also in-creases security. In this case, smart cards can be a solution as a physical medium in which the cipher keys and algorithms can be kept in safety and secrecy [16]. Smart cards are stamp-size computer models with Central Processor, Memory Areas, I/O control areas [1]. With a card as large as a credit card, smart card applications are widely used in transportation, health, banking and finance, identity, security, labeling, passport and in many other areas [7]. The most important advantage of smart card is its pocket-size and that it supports all these applications with the top security criteria it meets. One reason why smart cards are highly demanded is that one card can be used for many applications. When the security mechanisms of smart cards are integrated with the power of cryptography, it will be a breakthrough [16]. In this study, the size of the keys used in encryption algorithms in cryptology will be magnified to make them more difficult to guess besides these big keys will be hidden in smart cards, making them secret for users. In this way a more robust and reliable cryptographic process is achieved.
2. Material
2.1. Smart Card Reader-Writer
In our application, we used Omnikey Cardman 1010 card reader writer was used. This device performs communication via RS232 serial port. The device uses PS-2 port of the computer as power source. The current it draws during the study is 60 mA. The cable length of the device is 180 cm. The communication speed between the smart card connected to the device and the computer is 9600-115200 baud.
2.2. The Properties of the Smart Card
Smart cards we used in the application are contacted Starcos SPK 2.3 cards with microprocessor produced by Giesecke & Devrient company. This card complies with ISO/IEC, EMV 96 and ISO 7816-8 standards. It supports RSA, DES, 3DES algorithms for digital signature and data encryption [7]. The card is produced to have an application area of 32 Kbyte. Some of this area is used for the processing system and other applications.
Figure 1. Smart Card reader-writer
3. Application
3.1. Smart Card Control Program
The first applications developed to control smart card includes access to card, opening a file or document on the card, writing information on the card, reading information from the card, e-purse application with the card, I\O control like a turnstile, DES and 3DES encryption applications, blocking or unblocking card, changing PIN and PUK codes [16].
In the opening of the program, the condition of the smart card reader, the number of readers (more than one reader can be working at the same time), the name of the active reader, the connection situation of the card plugged to the reader is given in the upper part of screen of the program as shown in Figure 2. If any card is plugged to the reader and if it is not a system card, “Invalid Card” message appears. If the card plugged is s system card, in the part of the screen which shows the card condition, the message “There is a card in the reader! Connection with the card is achieved!” is shown. Besides, the card number (ID) of the card is shown on the screed. If the smart card to be connected to reader is a new card, in other words if it is an unformatted card, the box indicated as “New” is marked. Thus, new card can be processed as required.
Figure 2. Screen shot of smart control program
While a new card is formatted for this system, first of all the ciphers to be used to access card (User PIN, Admin PIN, PUK) are determined (Figure 3).The first User PIN, Admin PIN and PUK ciphers to be used for a new card are determined to be “0000” by the manufacturer. In this section of the program, old PIN and PUK ciphers are changed with new ones. If PIN is entered wrong 3 times, the card is blocked and the user can no longer reach the card. The User PIN can be changed by Admin pressing on “UNBLOCK CARD” button (Figure .4 ).
Figure 3. Changing PIN and PUK
codes Figure 4. Unblocking user PIN
Admin PIN and PUK ciphers can be tried 10 times upmost. If they are entered wrong for 10 times, the card is completely blocked and will not work again.
This is the first stage of security system of smart card technology. After these processing, Personalization process of formatting is started (Figure 5).
Figure 5. Personalization process
Personalization process is performed to form the files and the directory of these files which are neccessary to write and read information and to determine the size of the directory and the files. For writing and reading to the file process to be performed, the directory is to be chosen after it is opened. After these processes are finished, the file is to be definitely closed. Otherwise, the processes performed will not be counted to be valid. When determining directory and file names, an address in the memory is to be given in hexadecimal way. As 3F00, 3F01 and FFFF directories are system directories for this card; they cannot be created by the user.
In create a E-purse section, e-purse file is formed by giving it a file name after the directory is chosen. No file size is defined for this file. The counter in an e-purse can count up to maximum 2.147.483.648, which is determined by the manufacturer. This value cannot be a negative value. After that we can perform writing and reading in the directories created on the smart card (Figure .6).
Figure 6. Reading and writing processes on the smart card
In this section, we are to make sure that the directory and the file to written is chosen After “choose directory and file” processes in personalization process is done, the directory and file are given beginning address and writing process is realized. Depending on the size of the file, the end address is automatically cal-culated. Reading process like writing process is performed by pressing on “Read the file” and “Read the file ex” buttons after directory and file are chosen and starting and end address are given. “Read the file” button can read maximum 110 byte data. To be able to read larger data “Read the file” button is to be used.
In e-purse processes, the amount of credit is written the section “Enter the amount” section. The amount of credit is increased with “E-purse +” and decreased with “E-purse —”. With “Read” button the amount of credit is shown in “Credit” message (Figure 6).
If smart card plugged to the reader device belongs to someone who has not been defined before (an area of 100 byte was opened in file 5 in the directory at 3F03 address and user information was written. E-purse information is in number 6 file), information about this person is seen on the screen (Figure 7). Later on, processes on the user card can be made.
Figure 7. User information 3.2. Smart Encrypt
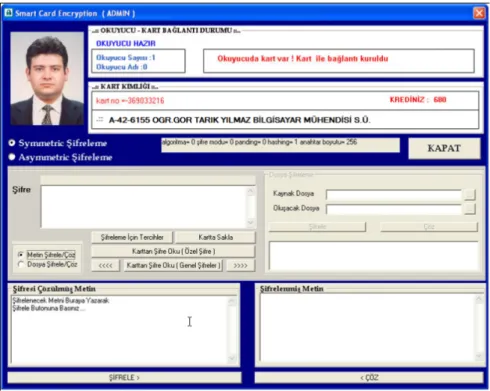
In the second application which includes the use of symmetric and asymmetric encryption algorithms [15] on smart card identity recognition, extraction of person’s credit after each use as a part of e-purse application, encryption of text or file using symmetric encryption and text encryption processes can be performed [16].
Figure 8. Smart encryption
After smart card encryption application program is started, first of all the con-dition of the reader and the concon-dition of the card plugged to the device are seen on the screen (Figure 8). The number of the reader device and the name of the active reader, whether smart card is plugged or not are given on “reader-card connection condition” screen. After the card is plugged, “User Long-on” win-dow is shown on the screen. At this stage, either “USER” or “ADMIN” users, which have been previously defined, is entered. Later on, password for the user is required [4] (Figure 9).
Figure 9. User logon
After one logs on the system, user information, card number, user photo and credit information are seen in “Card ID” section. Each time one logs on the system, credit amount is reduced by 10 credits. User whose credit is used up cannot enter the system and needs credit to be reloaded (Figure10).
Figure 10. Entrance to the system
When one logs on the system as “ADMIN”, all functions are active. All processes like creating password and writing encrypts on the cards. For security reasons, only one person is to be “ADMIN”. This person gain access to smart card as “ADMIN” as well. In this case, either symmetric or asymmetric encryption option is to be preferred. After symmetric encryption is chosen, Figure 11 is shown on the screen.
Figure 11. Symmetric encryption
In symmetric encryption section, two types of encryption and decryption process are realized. These are text encryption/decryption and file encryption/decryption processes. For symmetric encryption “Secret Key” is determined by the admin-istrator and is written in the encrypt box [14]. Later on, this key is to be saved on the card by pressing on “Save to the Card” button. All cards to use this system, the same secret key (encrypt) is to be written.
By pressing on “Read Encrypt from the card (special encrypt)” button, secret key on the card can be read. From now on encryption for everyone who uses the system will be dome with this secret key (Figure 12-a). From “Read Encrypt from the Card (General Encrypts)” section, “public key” used in asymmetric encryption can be used as “ secret key in symmetric encryption (Figure 12-b). The owner of the public key is shown in the upper part as a message.
Figure12a. Reading secret encrypt for the group from the card
Figure12-b. Using public key written on the card and used in asymmetric encryption as a secret encrypt
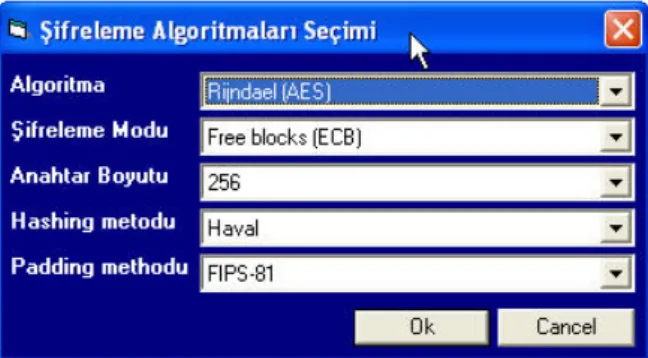
To choose the algorithm to be used in encryption, it is necessary to press “op-tions for encryption” (Figure 13)
Figure 13. Choosing encryption algorithms
In this section, the algorithm to be used for encryption (Rijindael (AES) (0), TwoFish (1)), Encryption Mode (Free Blocks (ECB) (0), Chained Blocks (CBC) (1)), Key Size (128-192-256), Hashing Method (SHA1 (0), Haval (1)) and Padding method (FIPS-81 (0), RFC 1423 (2), Random (1)) is chosen [12][17]. After algo-rithm is chosen, in the upper part, the methods chosen are indicated as “0-1-2” as a message. Text encryption choice is marked, the text written in the text box is encrypted according to the method and secret key (Figure 14).
When file encryption choice is marked, firstly the file to be encrypted is chosen. After that, depending on the method chosen and secret key, it is saved with *. tae extension or with *. t2f extension. Meanwhile, the extension and the codes from encryption choices are added to the encrypted file (Figure 15). For example, when “trial. doc” file is encrypted, the encrypted file is named as “trial _doc 0 0 0 0 256. tea”. Here _doc indicates that this file is a word document, the 1st parameter (0) from the left indicates that “type of algorithm” is “AES” (1 indicates “Twofish” algorithm ), 2nd parameter (0) and that ‘encryption mode’ is “free blocks” (1 shows “chained block”), 3rd parameter (0) shows that “panding method” is “FIPS” (1 indicates “random”, 2 indicates “RFC 1423”), 4th parameter(0) shows that “hash” method is “SHA” (1indicates “HAVAL” ).
Figure 15. Symmetric file encryption
When asymmetric encryption choice is marked, the image in Figure 16 is seen. In this encryption method, RSA encryption algorithm is used [5][9].
In this section, two keys, Private Key and Public Key, are used [10]. For this reason, a file is to be opened to create a Pair of Keys. These files have *. Key extension and previously created files. After these files are chosen, the size of the key is determined with “Create a Pair of Keys” button and a pair of keys is formed and these keys are kept both in the file and shown in the text box in the lower section. The size of pair of keys is a maximum of 1024 byte because key is prepared according to the size of the files to be written. If demanded, the size of the key can be increased by increasing the size of file. The drawback of this is that it decreases the number of system users (Figure 17).
A Pair of key is to be made for each user. For each user, pair of key is written on the card by pressing on “save pair of keys to the card” button. For public keys of other users to be written on the card, after open key files of other users are chosen, “open the key from the file” button is pressed. Later on the name of the user is written in “write your name” section and public key is loaded by pressing on “load public (user)” button. The public keys and users own pair of keys for all users are written on the card in this way ad it is compulsory.
Figure 17. Adjusting key size to create pair of keys
After all these processes are completed, we can now enter the text to be en-crypted and pair of keys of the user is loaded by pressing on “Read cipher from the card Private/Public” button. Later on, the public key of the person to whom we will send the text is reached by pressing on arrow keys (“<<<<”, ”>>>>”). Thus encrypted text can be deciphered only by this person. All encrypted texts created are sent to the receiver through an open link, e.g. us-ing any software on the internet or computer. The receiver presses on “ Read Cipher from the card Private/Public” button after plugging in his/her smart card to the reader and entering required user ciphers. After the keys are read, the reader presses on “Decipher” button and the text is turned into normal text (Figure 18).
Figure 18. Asymmetric decryption
4. Results and Suggestions
The software developed in this study lead to a stronger and safer data commu-nication system by using the power of science of cryptography and smart card technology. With this study, files in our local computer can be protected and encrypted files can be sand safely. The fact that even the main user cannot know cipher key as the size of the keys on the smart cards is large and thus impossible to keep in mind increases the systems security. Even in case an unauthorized person captures files in information transfer or storing stage, they will not be able to read the files as they do not have smart card in which decipher keys are kept. By the same token, using the editor in the software instant messages can be sent safely using public sources ( e.g. hotmail, gmail, live messenger etc.) on the internet or intranet by encrypting them with keys in smart cards. Mes-sages can be read by the users who have cards in which decipher key is loaded, which is a proof for the fact that secure data communication can be achieved in every environment as in instant data communication, it is not possible for third persons to read messages. Besides, computers keep and save messages as cookies using processing systems. As the information saved with the method we have proposed will be encrypted texts, it will not be possible to read them even if they are obtained. In case the communication line is eavesdropped, message cannot be understood as information is encrypted.
It has been demonstrated that this system can be used in the security of com-puters and files in local networks and in messaging on the internet and e-trade. The results of the study and the suggestions for further studies can be listed as follows:
1. As a result of this study based on smart card, AES, TwoFISH, RSA algorithms were used and keys of as many bytes as required were produced to develop smart card based text and file encryption and keys were hidden in cards, which made the system more secure by preventing the user to reach the key. The security mechanisms of both smart card and encryption techniques were combined and our study created a medium more secure than its counterparts.
2. This study can be safely used anywhere from local computer networks to the internet requiring secure information transfer.
3. The disadvantage of this smart card based system is that the useable memories of smart cards are filled in with keys and identification applications. The number of the users that can use the system depends on the size of the keys and other applications. In the application, as the aim is to enable smart card user to use the program on any computer without needing any additional file or software, public keys which are used in asymmetric encipherment which occupies the largest space in the card are written in the card. If this information is kept in an additional file, limitation on the number of users will be eliminated. However, in this case, users will have to use the smart card on the computer in which the software and additional file is uploaded.
4. As the byte of the keys used in encipherment increases, the processing speed of the system slows down. On the contrary, system security has increased. 5. It was determined that smart cards sensitive to physical strikes and especially contacted cards are vulnerable to oxidation.
6. Cryptology product development is a field of study on its own and is f great economic values.
7. Smart card based encipherment software is to be absolutely used in public institutions in the transfer of national secret information.
When the results are examined , security is not only composed of solutions like anti-virus software, fire wall, Intrusion Detection and VPN, provision of basic components of security like data security, identification/confirmation of persons and protection of data integrity on the internet and computer networks is also very important. The solutions and concepts that realize this are to be developed based on smart cards because of their pocket-size and high level of security. In systems in which Smart Card is used, there is a continuous profit relation. These systems are currently the most reliable and secure systems. In this sense, smart cards will continue to gain acceptance in many areas, primarily in security applications. They have already become tomorrow’s technology. 5. Acknowledgements
This study is a part of Master Thesis titled “ Solutions of Safety Problems on SmartCards", Tarık YILMAZ, submitted by Selcuk University, Graduate School
of Natural and Applied Sciences, Department of Computer Science Education, Konya, Turkey, 2004.
References
1. Bayır, S. 2002, Methods in cryptography and their application in smart cards, Y. L., Dokuz Eylül University.
2. Bellovin,S.M. and Blaze,M. 2001, Cryptographic Modes of Operation for the Inter-net, Second NIST Workshop on Modes of Operation.
3. Coppersmith,D. ve ark. 1997, The Data Encryption Standard, Information Security Technical Report, Vol. 2, No. 2, 22-24.
4. CryptoAPI-http://www.microsoft.com/security/tech/crytoapi/
5. Erhan,M. 1993, Data encyption/decryption methods and software design of RSA algorithm, Y. L., ITU.
6. Forte,D. 1999, The Future of the Advanced Encryption Standard, Network Security, p.g. 10-13.
7. http://www.cardwerk.com/smartcards/ 8. http://www.olympos.org
9. http://www.rsa.com
10. Naccache,D. 1999, Padding Attacks on RSA, Information Security Technical Re-port, Vol. 4, No. 4, 28-33.
11. Omnikey http: //www.omnikey.com/en/home.php
12. Stinson,D.R., 1995, Cryptography Theory and Practice, CRC Pres http://www.cacr.math.uwaterloo.ca/~dstinson/CTAP.html
13. Pierson,C.Limited,Z.1998, Network Encryption, Information Security Technical Report, Vol.2, No.4, 62-65.
14. Torrubia,A. Mora,F.J. Martı,L. 2001, Cryptography Regulations for E-commerce and Digital Rights Management, Computers&Security, Vol. 20, No. 8, 724-738. 15. Uysal,E. 1998, RSA, DES ve MD5 tabanlı halka açık bir kripto sisteminin geli¸stir-ilmesi, Y. L., METU
16. Yılmaz,T.,2004, Akıllı kartlarda güvenlik problemleri çözümü, Y. L. Tezi, Sel.Uni. Institute of the Natural and Applied Sciences , Konya
17. Wright,M.A. 1999, The Evolution of the Advanced Encryption Standard, Network Security, 11-14