OF Ä
'ГіШІЕСТ; OSIMQ LIMEÄiаді ï л f· ·2ΐ ЯНйчіг’Ьаі 'ía :Aтш
А THS'Sr! Íí'.^^e.· ' W W . 'ü i J d - - ·■'. . .»=■ t;, -r ^ .;!;.···«|·ί . "Л·,· «!»«». “И·... i VJ .'s^ i :% s : ¡aá Γώ. r: · T ‘it/ít !}'K. /f jW ·’· ,f ■· C ' t-vr'“ ,·*·'“·-'■■- і·’***^· В Y ' «ΐ· · ^ ttau Η», л* Μ ; . >*, Ä'.’M» я Í"í fc tAPPLICATION OF THE CRITICAL PATH METHOD TO THE PLANNING OF A TECHNOLOGY TRANSFER PROJECT USING LINEAR
PROGRAMMING
A THESIS
SUBMITTED TO THE DEPARTMENT OF MANAGEMENT
AND THE GRADUATE SCHOOL OF BUSINESS ADMINISTRATION OF BILKENT UNIVERSITY
IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF BUSINESS ADMINISTRATION
By
ELlF EMlRLl MAY, 1993
ı s
I certify that I have read this thesis and in my opinion it is fully adequate, in scope and in quality, as a thesis for the degree of Master of Business Administration.
Assoc. Prof. Erdal Erel
I certify that I have read this thesis and in my opinion it is fully adequate, in scope and in quality, as a thesis for the degree of Master of Business
Administration. _^ _
J
Assi^.Prof.Gillnur §engül
I certify that I have read this thesis and in my opinion it is fully adequate, in scope and in quality, as a thesis for the degree of Master of Business Administration
Approved for the
Administration
Prof. Sübidey Togan
Graduate School of Business
< w u
ABSTRACT
APPLICATION OF THE CRITICAL PATH METHOD TO THE PLANNING OF A TECHNOLOGY TRANSFER PROJECT USING LINEAR
PROGRAMMING
ELlF EMlRLl
Master of Business Administration Supervisor: Assoc. Prof. ERDAL EREL
May 1993, 132 pages
The main purpose of this thesis is to utilize
the critical path method in the planning of a
technology transfer project by using linear
programming. LINDO software is practiced in
establishing the linear programming formulation and a matrix generator is written in C language to input the
formulation into LINDO format. In this way, the
schedule of the project is created, the completion time of the project is calculated and the activities forming the critical path are determined. Also by applying a
parametric analysis to the right-hand sides of the
constraints (activity durations) for the noncitical
activities, the times when the critical activities
became critical are determined.
ÖZET
BÎR TEKNOLOJİ TRANSFERİ PROJESİNİN PLANLANMASINDA DOĞRUSAL PROGRAMLAMA KULLANILARAK KRİTİK YOL METODUNUN
UYGULANMASI
ELİF EMİRLİ
Yüksek Lisans Tezi, İşletme Enstitüsü Tez Yöneticisi: Assoc. Prof. Erdal Erel
Mayıs 1993, 132 sayfa
Bu çalışmanın amacı, bir teknoloji transferi
projesinin planlanmasında doğrusal programlama
kullanılarak kritik yol metodunun uygulanmasıdır.
Doğrusal programlama formülasyonunun oluşturulmasında
LINDO yazılımı kullanılmış ve formülasyonu LINDO
formatına çevirmek için de C dilinde bir program yazılmıştır. Bu şekilde, projenin aktivite zamanları, proje bitiş zamanı hesaplandı ve kritik yolu oluşturan
aktiviteler belirlenmiştir. Ayrıca kritik olmayan
aktivitelerin zamanlarına parametrik analiz yapılarak bunların kritik yola girme zamanları elde edilmiştir.
Anahtar Kelimeler: Kritik Yol Metodu, Proje Planlama ve
Aktivite Zamanlarını Belirleme, Teknoloji Transferi,
I would like to thank to Assoc. Prof. Erdal Erel for his guidance, suggestions and encouragement
for the preparation of this thesis. I am also thankful
to Assist. Prof. Dilek Önkal and Assist. Prof. Giilnur
Şengül for their helpful suggestions during the
completion of the thesis.
My thanks are also due to Mrs. Özge Savaş, Mr. Ergun Bora and my colleagues in ASELSAN for their supports and understanding throughout the thesis. I am indebted to ASELSAN Military Electronics Inc. for the facilities provided.
I would also like to express my deepest
gratitude to my family; Doğan, Nevin and Mustafa Emirli for their continuous supports not only during the thesis but also throughout my education in Bilkent University.
TABLE OF CONTENTS PAGE ABSTRACT...ii Ö Z E T ... iv ACKNOWLEDGEMENTS... v TABLE OF CONTENTS... vi
LIST OF FIGURES ...ix
CHAPTER 1 : INTRODUCTION... 1
1.1. Scope of the Study... 1
1.2. An Overview of the Technology Transfer Concept... 2
1.2.2.Types of Technology Transfer Channels... 3
1.2.2.1. Trademark Transfer... 4
1.2.2.2. Patent/Patent License Transfer... 4
1.2.2.3. Technical Information (know-how) Transfer .. 5
1.3. An Overview of the Project... 8
1.3.1. License and Know-how Transfer Activities... 9
1.3.2. Hardware Supply Activities... 10
1.3.3. UTTE Supply Activities... 14
1.3.4.Sales Contract Activities with the Customer .... 14
1.3.5.Activities inside the company... 15
1.4. Purpose of the Thesis... 15
2.1 .Historical Background... 18
2.2.Overview of Project Management... 20
CHAPTER 3 : LITERATURE SURVEY...25
3.1. Project Scheduling Techniques... 25
3.2. Bar Charts... 25
3.3 .Logic-Diagram-Based Schedules... 26
3.3.1. Advantages/Drawbacks of CPM over Bar Charts .... 28
CHAPTER 4 : NETWORK MODELS IN SCHEDULING... 30
4.1. Critical Path Identification...30
4.2. Basic Definitions... 31
4.3. CPM Scheduling... 33
4.3.1 .Activity Relationship Methods... 33
4.3.1.1 .AOA M e t h o d ... 33
4.3.1.2 .AON M e t h o d ... 37
4.3.1.3.The Precedence M e t h o d ...38
4.4. Finding a Critical P a t h ... 39
4.4.1. Critical Path Identification with L P ... 39
4.4.2. Applying Linear Programming to the Schedule .... 41
4.4.3. Matrix Generators...43
4.5. Parametric Analysis... 44
4.5.1.Types of Parametric A nalysis... 45
CHAPTER 5 : APPLICATION OF CPM TO THE TECHNOLOGY TRANSFER PROJECT...4 6 5.1.Identifying Activities/Estimating Their Duration ... 46
5.2 . Preparing the Schedule... 48
5.3. Identifying the Critical Path Activities... ..50
5.4. Applying Parametric Analysis to the Activities... 51
5.5. Discussion and Evaluation of the Implementation .... 53
CHAPTER 6 : CONCLUSION AND RECOMMENDATIONS... 55
6.1. Conclusion...55
6.2.Suggestions for Further Research... 63
LIST OF REFERENCES...66
APPENDICES A. LINDO COMPUTER PACKAGE...68
B. MATRIX GENERATOR PROGRAM FOR LINDO FORMULATION... 73
C. ACTIVITY L I S T ... 75
D. LINDO FORMULATION... 105
E. PARAMETRIC ANALYSIS RESULTS OF THE NONCRITICAL PATH ACTIVITIES...119
LIST OF FIGURES
PAGE
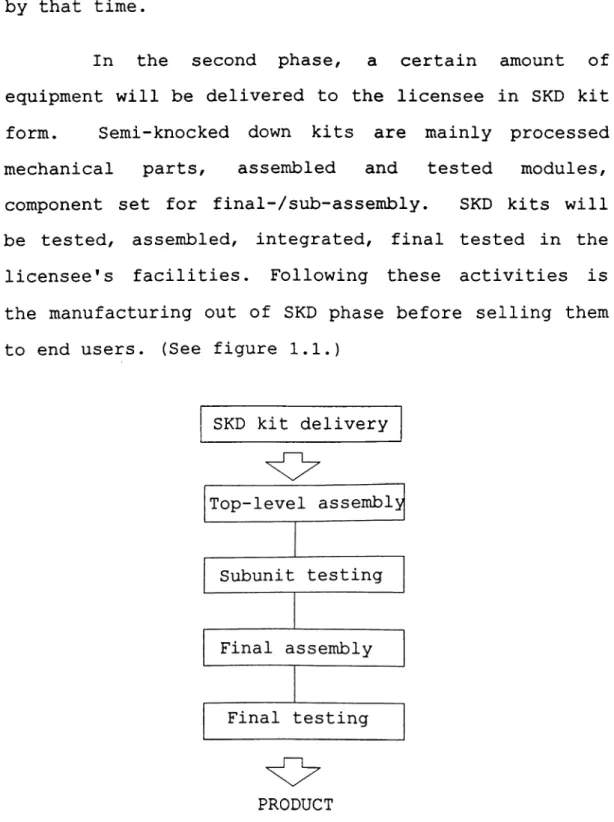
Figure 1.1. Flow chart of SKD phase production... 11
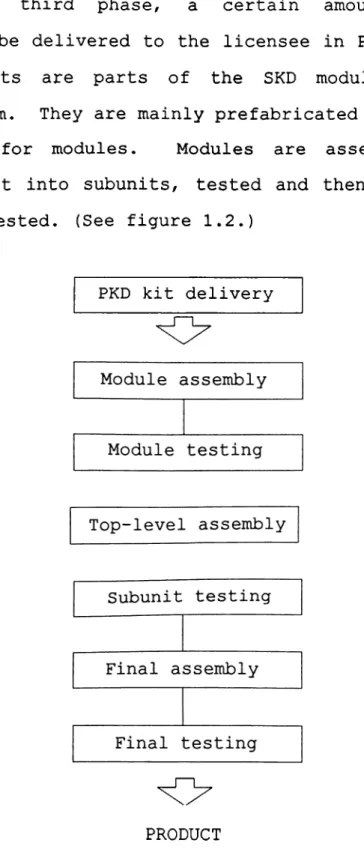
Figure 1.2. Flow chart of PKD phase production... 12
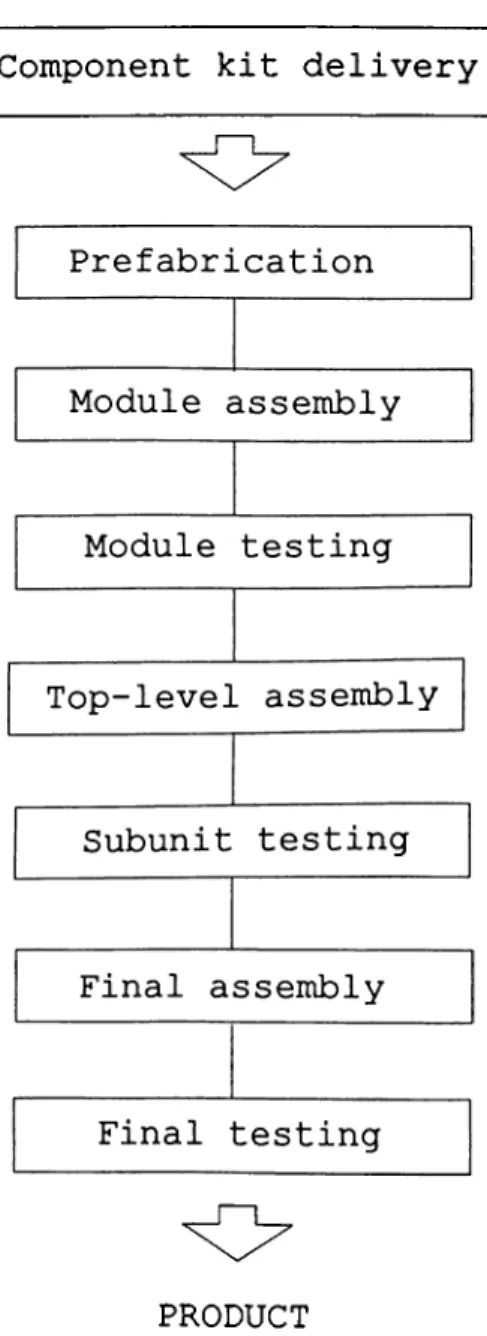
Figure 1.3. Flow Chart of Production from Component... 13
Figure 4.1. Single activity in AOA format...34
Figure 4.2. Activities with a Dummy Constraint... 35
Figure 4.3. Violation of Rule 5 ...36
Figure 4.4. Use of Dummy Activity... 37
Figure 4.5. AON format...37
CHAPTER I
INTRODUCTION
1.1.Scope of the Study
"Project management is not only a science but
also an art. It is a science because it makes use of
scientific techniques that have been proven to enhance
management processes. It is an art because it relies
on the judgment, expertise and personal intuition of the project management people." (Whitehouse,1973,1989)
Leaving the art side of the project management aside, the emphasis is on science part of it in this thesis.
Most of the scientific techniques available to project management people are handled with the help of
computer hardware and software. Although project
management makes use of computers in many areas such as
project planning and organization, project
coordination, project control, budget analysis and
project communications; activity scheduling and
resource allocation are the areas where computers are utilized most.
And the scope of this study is limited to project scheduling with critical path method (CPM) by
making use of linear programming software LINDO. The
discussions are also applied to a technology transfer project as an illustration.
1.2.An Overview of the Technology Transfer Concept
The fast development of global
industrialization has brought a new approach to the
concept of ownership in law in the last centuries and consequently besides tangible rights, intangible rights
also emerged. Technological knowledge, which is gained
either as a result of experience or as a result of systematic research, had become something that is sold
in return of money. It has long been a very common
behavior to buy the results that some other company developed by paying a suitable fee which is called
transfer of technology. The transfer of technical
information related with the design, engineering,
manufacturing, and production techniques for hardware systems using recorded and/or documented information of a scientific or technical nature is called technology
transfer. (the Defense Systems Management College
Publications,1987)
With the rapid widening of the technological gap between the developed and developing countries, the
transfer of technology has become a matter of decisive
importance. This importance is not restricted to the
developing countries alone, but to the developed ones
as well, since no industrial, trade or cultural
relations can be built up and maintained between the two, without bridging, or at any rate reducing this
gap. (Bhattasali,1972) Hence, although technology
transfers may be among companies from different
countries or among companies from the same country, the most common type is the one which includes different
countries. In other words, transfer of technology is
an integral part of national development.
Technology transfer is indeed an extremely
broad subject and it is perceived as an increasingly important ingredient in the development of industrial
resources and wealth. Technology transfer enables
companies to make better use of their scarce resources of research and development for donor companies in that it provides additional income to be derived from R & D. On the other hand, it represents a source of new and improved products in an increasingly competitive world for the recipient companies.
1.2.2.Types of Technology Transfer Channels
Although technology transfers vary in their
transfer, patent/patent license transfer and technical information (know-how) license transfer for them.
1.2.2.1.Trademark Transfer
Trademark is a sign which is put onto a product or to its package in order to distinguish it from the
similar products. Trademarks are registered by the
government to hinder unfair competition by
counterfeiting. (Milli Prodüktivite Merkezi, 1975) Any
other company can obtain the rights to use the
registered trademark of a company by paying a suitable fee to the owner of the trademark.
Contracts are made between the companies for
the transfer of trademarks. These contracts should
also be approved by the government office which
registered the trademark. In these contracts there
exists issues such as the term of the agreement, the products for which the trademark can be used and whether the trademark is transferable or not.
1.2.2.2.Patent/Patent License Transfer
Patent is a grant of specific monopoly rights given by a government to an inventor for his invention that is valid for a certain period of time and only within the territorial limits of the country in which
it is granted, (the Defense Systems Management College
Publications,1987) These rights can be transferred in
return of a fee which is called patent transfer. If
only the rights to use the patent but not the rights to transfer, are transferred then this is called patent
license transfer. (Milli Prodüktivite Merkezi
Yayınları, 1975)
In patent/patent license transfer contracts , there exists topics such as what portion of the patent is transferred, if the licensee is given the right to transfer and whether the developments, if any, will also be transferred to the licensee.
The monopoly granted to the patentee rules the others out from using the particular invention in the sense that it provides redress by giving the right to bring suit but it cannot prevent the direct violations.
1.2.2.3.Technical Information (know-how)
Transfer
Know-how is an American term which is receiving growing acceptance in international contracts. It is a
generic term and it includes trade secrets,
manufacturing procedures and techniques,
specifications, charts, formulae, drawings and graphs, marketing techniques and professional advice and the
like except patents and trademarks. Actually know-how can be anything which is not readily known or available to the public.
The Restatement of Torts defines know-how as
"any formula, device or compilation of information
which is used in one's business and which gives an opportunity to gain an advantage over competitors who do not know or use it." (the Defense Systems Management College Publications, 1987)
Therefore, know-how can be similar to a patent in the sense that it grants some kind of monopoly by preventing those who do not posses it from using it. But it is also differentiated from patents in the
following issues (the Defense Systems Management
College Publications, 1987) :
. The monopoly is de facto as opposed to de jure.
. The monopoly is maintained indefinitely unless the know-how is made public.
. What is essential to the value of know how is some extent of secrecy.
There is a current trend of switching from
patent system to know-how rights to protect the
recent years. Furthermore, know-how is generally
necessary to utilize the patents licensed in an
agreement. As a result of this, another common behavior in this area has been to contain only know-how without patents in the licensing agreements.
The companies that are successful in
transferring technologies to other companies have a
common belief in general. This belief is that the
beginning of a successful local production is not at the time of contract signature between two parties, but it is as early as the time the design goals for a new product or system to be transferred later are being
defined. One design goal of such a product is that it
must be producible in foreign countries autonomously,
free of bottlenecks and hindrances. In order to do
this, the product should be designed taking the
availability of components in the world market into
consideration. Furthermore, the local manufacturing
philosophy should be structured in a modular way to enable the company receiving the technology to increase the local manufacturing content step by step thus
achieving the implementation of the full know-how
transfer to a 100% autonomy in subsequent modules, parts and components at the earliest time possible.
1.3.An Overview of the Project
The Project is mainly a license and know-how transfer of a defense product from a European company and subsequent manufacturing of it in the licensee's facilities and then selling it to a customer in Turkey. The licensee company is a Turkish company and the
project duration is 7 years. The overall project
involves 3 agreements and a contract, namely License
and Know-how Transfer Agreement, Hardware Supply
Agreement, Unique to Type Test Equipment (UTTE)
Agreement and Sales Contract. While the three
agreements are between the licenser which is a
multinational company and the licensee ; the contract
is between the end customer and the licensee.
In this program, the licenser is selected by the customer from a number of foreign companies which are manufacturing the product the customer desires to buy. The licenser possesses some specific proprietary rights, manufacturing rights and certain engineering and production know-how essential to or helpful in the manufacturing the product. Following the selection of the licenser, the customer has opened a domestic tender for the local production and delivery of the product. It obligated the bidders for the tender to locally
product and provide the necessary support.
A contract is signed between the customer and the winner of the domestic tender. The licensee has
been nominated by the customer for the local
manufacturing of the product and had obtained the
rights to use, to manufacture, to sell and to provide maintenance for the product and subassemblies of the product in accordance with the License and Know-how Transfer Agreement.
Although the validity of the agreements in consideration lasts 7 years, only the activities of the first 3 years will be studied in this thesis due to the
data available at hand. Besides, activities after the
third year will be a repetition of the first 3-year activities.
Since the project is in the defense industry, confidentiality agreements are made between the two parties to protect the proprietary rights. And because of these agreements, the name of the licenser and the licensee, the name of the product any other information about it will not be disclosed within the thesis.
1.3.1.License and Know-how Transfer Activities
These are the activities of the License and Know-how Transfer Agreement signed between the licensee
and the licenser company. They mainly consist of training courses at different phases of the project, technical assistance programs and delivery of technical
and manufacturing data package activities. This
technology transfer is planned be completed by the end of 1997. In order for the licensee to be able to manufacture the product in its own facilities, the timing of the activities in the technology transfer must be closely monitored. Namely, the success of the project depends on the timely and successful progress of technology transfer activities.
1.3.2.Hardware Supply Activities
These are activities of the Hardware Supply Agreement signed between the licensee and the licenser
company. While the license and know-how transfer
continues between the two parties, the procurement of necessary kits and components from the licenser also continues according to the provisions of the Supply Agreement.
In general, they consist of procurement
programs of ready made units (RMU), semi-knocked down
kits (SKD) , partly knocked down kits (PKD) and
components. In the early phases of the program, a
number of RMUs will be procured from the licenser and will be sold to the customer without giving any
additional value to them since necessary technology will not be present in the facilities of the licensee by that time.
In the second phase, a certain amount of
equipment will be delivered to the licensee in SKD kit
form. Semi-knocked down kits are mainly processed
mechanical parts, assembled and tested modules,
component set for final-/sub-assembly. SKD kits will
be tested, assembled, integrated, final tested in the licensee's facilities. Following these activities is the manufacturing out of SKD phase before selling them to end users. (See figure 1.1.)
SKD kit delivery
O
O
PRODUCT
In the third phase, a certain amount of equipment will be delivered to the licensee in PKD kit
form. PKD kits are parts of the SKD modules in
unassembled form. They are mainly prefabricated parts,
component set for modules. Modules are assembled,
tested and built into subunits, tested and then final assembled and tested. (See figure 1.2.)
PKD kit delivery
O
PRODUCT
In the last phase of the supply program, some must-buy items will be procured from the licenser and other material will be procured from other vendors.
Items delivered in this phase are mainly raw material for prefabricated parts and modules and some component kits.
Component kit delivery
O
PRODUCT
Component kits delivered in this phase are
prefabricated and built into modules. Then the same
operations as in PKD phase are performed from this stage onwards. (See figure 1.3)
When the term of the agreements expired, the complete purchasing of materials will be done by the
licensee. The received material from the suppliers
will be tested in the incoming inspection department of
the licensee. But the scope of this thesis covers only
the activities during the first 3 years of the
agreement. However, the success of this independent local production phase depends on the timely and
successful transfer of technology satisfying the
requirements of the original product.
1.3.3.UTTE Supply Activities
These are the activities of the Unique to Type
Test Equipment Agreement. They mainly consist of the
procurement of the special equipment which are not components of the product but are specially used in the manufacturing and testing of the product.
1.3.4.Sales Contract Activities with the
Customer
between the licensee and the customer. They mainly consist of the deliveries of the product in batches
beginning in 1992, ending in 1994, and operator
training, field level maintenance training and depot level maintenance training programs that will be given to the customer.
1.3.5.Activities inside the company
These are the insider activities that will be performed by the licensee in addition to the other agreement and contract activities. They mainly consist of the procurement of standard equipment, procurement from the other vendors, building SKD production set-up,
building PKD production set-up, building local
production set-up, building UTTE production set-up and local production phase.
1.4.Purpose of the Thesis
Technology transfer projects, like other
projects, consists of a number of activities. But the
feature that differentiates technology transfer
projects from others is the existence of strict
deadlines to be satisfied. Therefore, they necessitate
close monitoring. For example, in order to complete
the technology transfer project subject to this thesis and to perform the subsequent local manufacturing phase
on time and with success, bottlenecks and potential problem areas should be identified before they occur.
For this concern CPM is one of the useful and
economical methods in scheduling. The purpose of this
thesis is to show how CPM using linear programming can be applied to the scheduling of a technology transfer project.
1.5.Outline of the Thesis
In this chapter, first of all, technology
transfer concept is explained and then some brief information is given about the particular technology
transfer project. Following this chapter, project
management concept is explained including its
functions. One of these functions which is project
scheduling is the subject of the third chapter giving
the literature survey on the different scheduling
methods such as bar charts, PERT and CPM in a
comparative way. In the fourth chapter, network models
in scheduling is explained with emphasis on Activity on
Arc (AOA) method which is the one used in CPM. These
led the discussion in chapter four to finding a
critical path by making use of linear programming. In
the fifth chapter, the methodology used in the
particular application is explained. The critical path
on the schedule is conducted in this chapter. Conclusion and recommendations are given in the sixth chapter.
CHAPTER 2
PROJECT MANAGEMENT
2.1.Historical Background
Although project management has been used in industrial capital projects for more than 50 years, it
gained widespread usage in many areas such as
construction, banking, manufacturing, marketing,
healthcare, sales, transportation, and research and
development as well as academic, legal, political and government establishments in the recent 10 years of time due to the successful results obtained in the capital projects field.
Project management applications were initially
concentrated on defense-related and construction
projects and many of the important developments in project management area occurred during and immediately after the World War II. One of the first publicized successes of the project management was the famous Manhattan project. It started early in the 1940s to develop the atom bomb under the direction of General Leslie Groves who is qualified as the first project
manager. (Ritz, 1990)
Following World War II, substantial
improvements on the capital projects side are realized both in size and monetary value. This was nothing but a result of the post-war economical boom which is seen all over the world. As a result of the trials to
reconstruct Europe and to meet restrained demand
because of wartime restrictions, capital project
investment spending is increased substantially.
Consequently, project management studies accelerated in order to meet the huge demand for new plants.
The 60s was the period which had taken the most of capital project increases of the post-war era especially with the construction of office buildings,
airports, power plants, chemical plants, holiday
centers and the like. Whereas in the 70s, the
economical expansion continued with runaway inflation
added to the trend. Also there was a growth in overseas projects of US. (Project Management Institute, 1981)
This era of super- and mega projects faded with the recession of 1981-82 and industrial plant usage declined to 70% from 85%. Nevertheless, the most important advantage gained from this era was that the top management people accepted the need for project management. (Cleland, 1983)
In the 80s, market expansion is observed in
high-tech field which includes electronics, foreign
autos, foods, biotechnology and the like. Accordingly, the size of capital markets lessened and the subject of
them became much more specialized. Hence they
necessitated more detailed project scheduling methods and expertised manpower.
The historical background of project managers indicates that the subject of project management is
subject to sudden changes. Thus it requires a
continuous awareness toward change and sufficient
flexibility in order to adapt to the environment on time.
2.2.Overview of Project Management
Project management is the process of managing, allocating, and timing resources in order to achieve a given objective in a expedient manner. The objective may be in terms of time, monetary or technical results. The term project involves several functions within itself such as project planning, project scheduling, resource management and project control.
Project planning is the first step in a
systematical project management study. It involves the
of a baseline plan. (Kerzner, 1984) During the preparation phase, this baseline plan is subject to many changes until it satisfies the overall objectives of the project. Project planning is performed in three organizational levels consecutively which are strategic planning, operational planning and planning by the line
and stuff personnel. (Cleland, 1983) Strategic
planning involves the high level selection of the project objectives by the top management or whoever the
strategic planners in the company. Operational
planning involves the detailed planning required to
meet the strategic objectives. Finally planning by the
line and stuff personnel puts the operational plan on a time scale by the strategic objectives enabling the execution of the project.
Project scheduling is the establishment of a
timetable to do work. It puts all the work activities
onto a timeline beginning at the project start date and
ending at the completion date. (Ritz, 1990; Levine,
1986) In order to achieve this objective, the schedule
should contain not only the list and duration of tasks but also the dependency relationship among tasks.
Experienced project management people favors
the top down approach in scheduling. In top down
approach first of all the list of major activities in
are broken down into sub macro activities and finally these sub macro activities are split into individual tasks forming the overall project.
Top down approach in scheduling is very
advantageous especially when there is a substantial amount of activities in the project because it helps people manage the overall project in a modular way
without getting lost in the sea of tasks. Furthermore,
it prevents people from missing some details while trying to cope with the whole bunch of activities at the same time.
After the project schedule is created, the
sequence of tasks in the project is established taking the planned duration of tasks and their dependency
relationships into consideration. Before doing this,
it is quite helpful to determine the immediate
predecessors and successors of the individual tasks.
Following the determination of the immediate
predecessor and successor relationships, all these are
connected in order to form the overall project
schedule.
Upon establishing the project schedule, some
milestones are defined on the schedule. Milestones are
zero duration tasks showing the beginning or end of
indicators of the achievements in the project and help the project management people evaluate the progress or
delay of the overall project. (DOD and NASA Guide,
1972)
Resources are the people and equipment needed
to get the tasks of the project done. And resource
management is the process of assigning and allocating resources to the individual tasks so as to meet the functional requirements of the project objectives.
(Badiru, 1989) While doing this, not only currently available resources but also the resources to be
procured must be identified. After that, the time-
based availability of resources should be specified so that resources could be allocated in a timely manner with no overloads or deficiencies.
Resource management plays a very important role especially in resource-driven projects and should be
closely monitored because in such projects the
structure and hence the performance of the project is
determined by the resources. (Fleming, 1987; Badiru,
1989)
Ensuing the schedule establishment and resource allocation, the costs of the tasks and resources in the
project is determined. Unexpected costs, in case of
consideration while making the budget of the project.
After all these phases are completed, the
project plan is reviewed. After this review, the ideas
and approvals of the related personnel is taken. Final
stage in project management involves the project
control activities.
This chapter has given a summary of project management and its functions in order to reveal where this particular study stands in the overall project
management subject. Narrowing down the topic, a
literature survey on project scheduling techniques is
CHAPTER 3
LITERATURE SURVEY
3.1. Project Scheduling Techniques
Two basic project scheduling techniques are bar
charts and logic-diagram-based schedules. Both methods
have their own advantages and disadvantages.
Therefore, selecting which technique to use is a very important decision since it also affects the success of the controlling phase of the project.
3.2. Bar Charts
Bar charts first came into use on capital
projects in the early twenties. The forerunner to the
bar chart was developed by an industrial engineer, Henry L. Gannt for scheduling production/operations
during World War II. Therefore, bar chart are the
oldest and the simplest of the scheduling techniques.
One of the advantages of the bar charts is their being cheap and simple to prepare, easy to read
and update. People with a little schedule training can
disadvantage is their inability to show enough detail to cover all the activities and their interaction on
larger, complex projects. That is the reason why they
become unmanageable on projects with as few as 100 activities. (Ritz, 1990)
Furthermore, bar charts cannot show clearly the interaction between early start and late finish dates of activities and the resulting float of non critical
activities. Hence, there is no clear identification of
the critical path through the project.
3.3.Logic-Diagram-Based Schedules
Although bar charts are simple and effective progress reporting tools, they are weak in planning. This, along with the fact that the size and complexity of the projects grew in the late fifties and sixties
obliged project management people add logical
relationships to Gannt charts. DuPont Company together
with Remington Rand (Univac) developed CPM (Critical Path Method) in 1957-1958 for planning and scheduling of plant maintenance and construction programs where the dominant emphasis was on controlling cost and
having schedule flexible. (Ritz, 1990/ Project
Mangement Institute, 1981)
of PERT (Program Evaluation and Review Technique) was invented by the Special Projects Office of the US. Navy in 1957-1958, and developed by Booz, Allen and Hamilton in conjunction with Lockheed Missiles Systems Division
on the Polaris Fleet Ballistic Missile Program.
(Project Mangement Institute, 1981) The dominant
emphasis in this program was on meeting closely
determined schedules for internationally strategic
reasons and taking a rather flexible view of cost control.
Today, the distinction between PERT and CPM had been disappeared and the two became nearly identical methods with slight variations in network format and
activity duration estimation. In the PERT, the
duration of an activity is calculated by assessing an optimistic and a pessimistic time and then calculating
the average of the two. (Moder,1983) Whereas in CPM,
there is only one value for each activity duration and it is the most likely time for the activity duration. Therefore, estimating the activity duration is a very important part in CPM scheduling since it directly
affects the critical path and the slack times. This
indicates the importance of getting the most
sophisticated estimates from the most experienced
specialists. Activity duration estimates should
this would skew the schedule too far one way or to the other.
3.3.1 .Advantages/Drawbacks of CPM over Bar
Charts
CPM is capable of handling many work activities
on complex projects. However, one should not use more
activities than necessary just because it is easy to do
so. In such a situation, the scheduler might get lost
in the details and use the activities in a less
efficient way. (Busch, 1991) Actually, this was the
trap that almost killed CPM in its early years. One
way to get rid of this may be to use bar-charts for less complicated areas in the schedule.
Another advantage of CPM is that it establishes an intangible force on the project team to divide the project into all its working parts and form an early analysis of the individual work activities as early as possible. (Moder,1983)
Disadvantages of CPM are a few in number and
can be avoided if proper attention is paid to. One of
these disadvantages is the necessity of the project people be trained in CPM techniques which is something
costly. All the people in the project team should
training includes all project management team including people from various functional departments.
On top of this, CPM generates more data than
bar charting. That means unit cost of the data in CPM
is low. However, if the data are not used or are being
improperly used, then the unit cost of the data is not low any more and the. project team is not getting the
worth from the particular investment on CPM.
(Ritz,1990)
This chapter has given a comparative literature
survey on the project scheduling techniques. Next
chapter further narrows down the topic to give activity
relationships in scheduling. It also introduces how LP
can be relevant in a project scheduling study in finding the critical path and performing parametric analysis.
CHAPTER 4
NETWORK MODELS IN SCHEDULING
4.1.Critical Path Identification
Identifying the critical path of a project is actually nothing but an optimization problem because the aim here is to minimize the time project takes to
finish. Most of the optimization problems can best be
analyzed by making use of a network representation. Among these network models are shortest route problems, maximum flow problems, minimum spanning tree problems, CPM-PERT project scheduling models.
If the duration of each activity is known with certainty, CPM can be used to determine the length of
time required to complete a project. CPM can also be
used to determine how long each activity in the project can be delayed without delaying the completion of the
project. If the duration of the activities is not
known with certainty, PERT can be used to estimate the probability that the project will be completed by a given deadline. (Winston,1991)
critical path in a project, CPM-PERT project scheduling
methods can be used. Furthermore, as the duration of
the activities in this particular project can be estimated quite certainly, CPM is chosen as the more appropriate method to utilize in scheduling the project activities.
Before discussing the CPM project scheduling, some basic terms used in describing network models will be explained.
4.2.Basic Definitions
Activity : A project operation or process that
requires resources and consumes some amount of time to complete.
Critical Path ; The sequence of activities
which determines the total completion time for the project.
Dummy Activity : A logical link or a constraint
representing no specific operation. It is an activity
which absorbs neither time nor resources.
Duration : The estimated or actual time
required to complete an activity.
Event : The completion of an activity, or a
Finish-to-start (F-S) : The condition that the start of an activity depends on the finish of its predecessors.
Finish-to-finish (F-F) : The condition that the finish of an activity depends on the finish of its predecessors.
Float : A time available for an activity or
path in addition to its duration. It is the difference
between the time necessary and the time available for an activity.
Network : The set of all project activities
graphically interrelated through the precedence
relationships.
Path : A series of connected activities between
two events.
Predecessor : A set of activities that must be completed before an activity begins.
Successor : A set of activities which can only
begin after an activity ends.
Start-to-start (S-S) : The condition that the start of an activity depends on the start of its predecessors.
4.3.CPM Scheduling
After identifying the list of activities that make up the project and their duration, it is time to
begin scheduling part of the baseline plan by
establishing activity relationships. Precedence
diagrams and precedence matrix are two of the methods
used to show these relationships. The activity
relationship method affects the schedule times to a
great extent. Hence, choosing which activity
relationship method to use in scheduling is an
important decision.
4.3.1. Activity Relationship Methods
There are three basic activity relationship methods which are AOA (activity on arc), AON (activity
on node) and the precedence method. CPM makes use of
AOA method in scheduling. Since the objective of this
thesis is to utilize CPM in project scheduling, AOA method will be discussed in more detail.
4.3.1.1. AOA Method
In the AOA, activities are represented by
directed arcs, and nodes are used to depict the
completion of a set of activities. In the arrow
event. The events are numbered sequentially and the activity is identified by the beginning and ending
event numbers. These numbers are designated as the i-j
number. (Lockyear,1984) With these definitions, a
single activity in AOA is as in figure 4.1.
O
Activity A DurationEvent(i ) Event(j)
Figure 4.1. Single activity in AOA format
Each activity has an elapsed time necessary to
accomplish the work involved. The estimated elapsed
time for the activity must consider the scope of the
activity and any historical data available from
previous similar activities. If there are no
historical data on the activity to estimate the
activity duration, then scheduling is done by using the estimates of the people experienced in performing the activity.
In the AOA format any activity may either precede, succeed, or be performed concurrently with any
other activity. A more complex situation depicted in
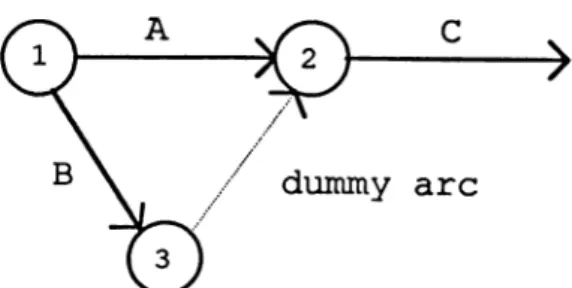
figure 4.2. specifies that A and B are prerequisites for activity D, but that only A is required to start
activity C. A dummy activity is drawn between event 3
constraints.
0
- ^0
- ^Figure 4.2. Activities with a Dummy Constraint
In figure 4.2. there are four real activities, indicated as 1-3, 2-4, 3-5, and 4-6, plus one dummy
activity, designated 3-4. A, B, C, and D are just
activity descriptions. Dummy activities are usually
indicated by a dotted line on the precedence diagram.
The following rules apply to the construction of a project network or precedence diagram in AOA format :
1. Node 1 represents the start of the project. An arc should lead from node 1 to represent each activity that has no predecessors.
2. A node representing the completion of the project should be included in the network.
3. Number the nodes in the network so that the node representing the completion of an activity has a larger number than the node representing the beginning
of an activity.
4. An activity should not be represented by more than one arc in the network.
5. Two nodes can be connected by at most one arc. (Winston, 1991)
Another use of dummy activities is to avoid the
violation of rules 4 and 5. For example, suppose that
activities A and B are both predecessors of activity C
and can begin at the same time. In the absence of rule
5, activity representation could be as in figure 4.3. However, since nodes 1 and 2 are connected by more than one arc, figure 4.3. violates rule 5.
Figure 4.3. Violation of Rule 5
By using a dummy activity as in figure 4.4., A and B both can be represented as the predecessors of C. Figure 4.4. guarantees that activity C cannot begin until both activities A and B are completed without violating rule 5.
Figure 4.4. Use of Dummy Activity
4.3.1.2.AON Method
In AON method the nodes of the network are used
to represent the activities. This method is widely
preferred in the recently developed project management programs prepared for microcomputers. (Levine, 1986)
Having activities represented in the nodes in AON format eliminates the need to use dummy activities
for unique relationships. Figure 4.5. illustrates the
same relationships that were shown in figure 4.2., but this time in AON format without any dummy activities.
4.3.1.3.The Precedence Method
The Precedence method is more complex than the
AOA and AON methods. Nevertheless, it permits a more
precise description of activity relationships in that it supports two additional types of relationships in
addition to the traditional finish-to-start (F-S)
relationships. These are start-to-start (S-S) and
finish-to-finish (F-F). (Bennett, 1977) Besides this,
the precedence method adds an element called ” lag ”, which is the time duration for the relationship itself.
(Moder, 1983) Lag is used either to indicate a delay
between the finish of one activity and the start of
another, or the delay between two starts or two
finishes.
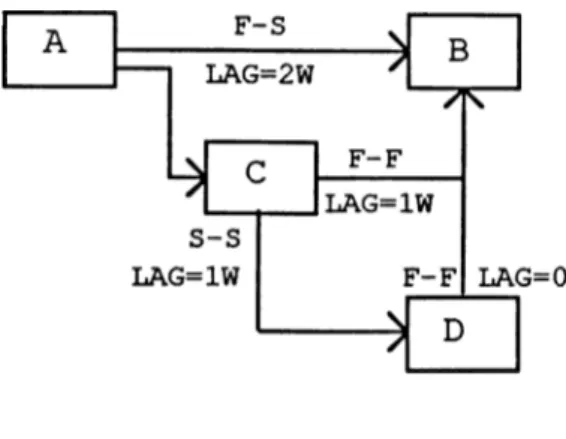
In the precedence diagram shown in figure 4.6., the start of task B is delayed for two weeks after task
A is completed. Task C can start after task A is
completed, but must be completed one week before task B
can be finished. Task D can start one week after task
Figure 4.6. PDM Format
4.4.Finding a Critical Path
Now that the list of activities making up the project is identified and AOA is chosen as the activity relationship method as a requirement of CPM, it is time to establish the project schedule, and find the critical path.
4.4.1.Critical Path Identification with LP
One of the ways of determining the length of the critical path in a project is by making use of
linear programming. Linear programming (LP) is a
mathematical decision-making procedure for determining
optimal allocation of resources. It has found
practical application in many areas of business.
In all LP problems the maximization or
there are also some restrictions or constraints that limit the degree to which the objective can be pursued. For most of the LP problems, there are two important
types of objects. The first type is limited resources
which can be time, money or labor and the second type
is set of activities. Each activity consumes some
amount or contributes additional amounts of resources. The problem in LP formulation is to determine the best combination of activity levels and which does not use more resources than actually available. (Schräge, 1991)
The problem to be solved is defined as the objective function, z in LP formulation and it can be either a minimization or a maximization situation as
explained above. The objective function is defined
using variables which are called decision variables.
These variables are all restricted to nonnegative
values. The activities consuming resources and the
scarcity of the resources are given as the constraints.
The solutions that satisfy all the constraints are referred to as feasible solutions and the best one among the feasible solutions is the optimal solution. The standard format of LP formulation is as follows :
Min (or Max) z = objective function subject to (s.t.)
constraint2 constraint^
all variables are nonnegative
LP applies only to situations in which the effects of the different activities which are engaged
in are linear. Linearity requirements are as follows :
1. Proportionality : Contribution of each
variable in the objective function or its usage of resources are directly proportional to the level of the activity.
2. Additivity : There should be no cross-
product terms in the formulation.
3. Certainty : All the parameters are known
constants.
4. Activity units can be divided into any fractional levels. (Schräge ,1991 ; Winston , 1991)
4.4.2.Applying Linear Programming to the
Schedule
While applying linear programming, first of
all, a variable called Xj is defined where Xj is the time that the event corresponding to node j occurs. For each activity (i,j), we know that before node j occurs, node i must occur and activity (i,j) must be
completed. This implies that for each arc (i,j) in the project network ,
Xj >= Xi + tij where t^j is the duration of
activity (i,j).
Above relationships are defined for each
activity and these constitute the constraints in the
linear programming model. Since the goal is to
minimize the time required to complete the project, the objective function in this linear programming model would be as follows :
z = X f - where X f is node that represents
the completion of the project.
Hence the complete linear programming model would be in the following form :
Min Z = X f - x^ st
Xj >= Xi + tij
for i=l to n, j=l to n & i not equal to j where n = number of events(nodes)
All variables integer
After including all of the project activity relationship constraints and the objective function into the linear programming model, it is time to solve
finding the critical path requires a large number of calculations for projects with hundreds of activities. Therefore, instead of manual calculation the model is run on a computer using a linear programming software.
In this thesis, LINDO is utilized as the linear
programming software package. (See Appendix A)
After the model is executed on a computer, the results of the model are used to determine the critical
path. Dual prices column of constraints is examined to
find the critical path. The critical path for a
project network consists of a path from the start of the project to the finish in which each arc in the path corresponds to a constraint with a dual price of -1. As explained in Appendix A, for each constraint with a
dual price of -1, increasing the duration of the
activity corresponding to that constraint by X days will increase the duration of the project by X days. Decreasing the activity duration will do the reverse effect as long as the activity remains critical.
4.4.3.Matrix Generators
Many linear programming models contain
thousands of decision variables. In such large LPs, it
is impractical to manually enter all the coefficients
and constraints of the LP. Instead of manual entering,
program called a matrix generator to simplify the
inputting of the LP. This program reads the problem
description in an arbitrary format from either a file
or from the terminal and then generates the
corresponding LP formulation depending on the given
information. There are two approaches in writing a
matrix generator program :
a. to use a general purpose programming
language such as FORTRAN, PASCAL or C.
b. to use a special purpose language designed
for generating LP formulations. These special purpose
languages are frequently available from vendors of LP optimization packages.
4.5.Parametric Analysis
After determining the critical path depending upon the solution of the LINDO formulation, performing parametric analysis may be quite helpful during the planning stage since it helps visualize the situation when assumptions upon which the model is based, is
changed. Parametric analysis or parametric programming
is the term applied to tracing out how the solution
changes as a specific coefficient (the parameter)
changes over a wide range.(Schräge, 1991) Most of the