T.C.
SELCUK UNIVERSITY
THE GRADUATE SCHOOL OF NATURAL AND APPLIED SCIENCE
RFID BASED ACCESS AND CONTROL SYSTEM WITH RASPBERRY PI
Osamah Salim Ahmed QASSAB MASTER OF SCIENCE
The Degree of Master of Science in Computer Engineering
March-2018 KONYA All Rights Reserved
I approve the above result
Prof. Dr. Mustafa YILMAZ FBE Director TEZ KABUL VE ONAYI
Osamah Salim Ahmed QASSAB tarafından hazırlanan “RFID Tabanlı Raspberry Pi ile güvenlik ve erişim kontrol sistemi” adlı tez çalışması 16/04/2018 tarihinde aşağıdaki jüri tarafından oy birliği ile Selçuk Üniversitesi Fen Bilimleri Enstitüsü Bilgisayar Mühendisliği Anabilim Dalı’nda YÜKSEK LİSANS TEZİ olarak kabul edilmiştir.
Jüri Üyeleri İmza
Danışman
Prof. Dr. Cemil SUNGUR Başkan
Dr. Öğr. Üyesi Ömer Kaan BAYKAN
Üye
DECLARATION PAGE
I hereby declare that all information in this document has been obtained and presented in accordance with academic rules and ethical conduct. I also declare that, as required by these rules and conduct, I have fully cited and referenced all material and results that are not original to this work.
İmza
Osamah salim QASSAB Tarih: 16/04/2018
iv ÖZET YÜKSEK LİSANS
RFID TABANLI RASPBERRY PI İLE GÜVENLİK VE ERİŞİM KONTROL SİSTEMİ
Osamah Salim Ahmed QASSAB Selçuk Üniversitesi Fen Bilimleri Enstitüsü
Bilgisayar Mühendisliği Anabilim Dalı Danışman: Prof. Dr. Cemil SUNGUR
2018, 64 Sayfa Jüri
Prof. Dr. Cemil SUNGUR Dr. Öğr. Üyesi Ömer Kaan BAYKAN Dr. Öğr. Üyesi Mehmet HACIBEYOĞLU
Günümüzde dünyadaki tüm ülkelerin ortak sorunu terör olayları ve onlara karşı alınan tedbirlerdir. Ülkeler, kurumlar ve kuruluşlar tarafından karşılaşılan güvenlik tehditlerine karşı otomatik tanımlama ve erişim kontrol sistemi uygulanması için çalışmalar yapılmaktadır. RFID, Radyo Frekansı Kimliği, güvenlik, varlık takibi, kişi izleme, envanter tespiti, erişim kontrolü uygulaması gibi çeşitli uygulamalar için uygulanabilen ucuz bir teknolojidir. RFID teknolojisi, otomasyon sistemlerinin bir parçası olarak çeşitli kuruluşlar tarafından yaygın olarak kullanılan olgun bir teknolojidir. Bu çalışmada, güvenlik amacıyla otomatik bir kontrol noktası sistemi tasarlanmıştır. Bu sistem, kişi ve ürünleri Ultra Yüksek Frekans-Radyo Frekans Tanımlama (UHF-RFID) yöntemiyle tanımlamak için tasarlanmıştır. Elde edilen bilgileri işlemek ve gerekli sinyali kontrol sistemine göndermek için Raspberry PI-3 mikrobilgisayar ve çevre birimleri kullanılmıştır. Ayrıca, yetkili kişilerin bilgilerini saklamak, silmek veya düzenlemek için Microsoft Azure ve web uygulaması kullanmıştır. Sistem; pasif alıcılar kullanılarak RFID okuma yöntemi ile elde edilen verilerin Web üzerindeki bir veri tabanında kayıtlı olan verilerle karşılaştırılması suretiyle çalışmaktadır. Elde edilen verilerle veri tabanındaki veriler uyumluysa, mikroişlemciye kontrol sinyali gönderilerek kontrol noktası açılacaktır. Alınan sinyaller veri tabanındaki sinyallerle uyuşmuyorsa, kontrol noktası kilitli kalmaya devam edecek ve sesli ikaz verilecektir. Ayrıca bir Wi-Fi bağlantı modülü üzerinden gerekli kişilerin cep telefonlarına bir uyarı mesajı gönderilecektir. Yapılan simülasyonlarda başarılı olduğu görülen bu sistem, kontrol/güvenlik noktalarında kullanılabilecektir.
Anahtar Kelimeler: Erişim kontrolü, Raspberry Pi3, RFID etiketleri, Uzun menzilli UHF RFID okuyucu.
v ABSTRACT MS THESIS
RFID BASED ACCESS AND CONTROL SYSTEM WITH RASPBERRY PI Osamah Salim Ahmed QASSAB
SELCUK UNIVERSİTY INSTITUTE OF SCIENCE AND TECHNOLOGY DEPARTMENT OF COMPUTER ENGINEERING
Advisor: Prof. Dr. Cemil SUNGUR Year, 64 Pages
Jury
Prof. Dr. Cemil SUNGUR Asst. Prof. Dr. Ömer Kaan BAYKAN Asst. Prof. Dr. Mehmet HACIBEYOĞLU
Today, the common problems of all the countries in the world are terrorist incidents and measures taken against them. A work has been devised so that an automatic identification and access control system can be implemented from the security threats that countries, institutions and organizations face. RFID, Radi0 Frequency Identificati0n is a cheap techn0l0gy, can be applied to many applicati0n like security, pe0ple tracking, invent0ry and g00ds detection, accessing contr0l application. RFID techn0l0gy is a developed techn0logy widely depl0yed by vari0us 0rganizati0ns as part of automati0n systems. In this work, an automatic control point is designed for safety purposes. In this system, it is designed to identify people and products from a distance by Ultra High Frequency - Radi0 Frequency Identificati0n (UHF-RFID) method. Where Raspberry PI-3 microcomputer and peripherals are used to process the obtained information and send the necessary signal to the control system. Also, we used Microsoft Azure and web-application to store, delete or edit the Authorized people’s information. The operation of the system is starting from the passive receivers, reads the RFID tag and this data is compared with the data that loaded on the database of Microsoft Azure. If the obtained data is compatible with the comparison data that in the database, the microprocessor is provided with the control signal and the switching point is opened. If the received signals do not match the signals in the database, the system control point is locked and audible. Behind this is a Wi-Fi connection module which sends a warning signal to the mobile phones of the required persons. As a result of the tests made, it was seen that the system was successful. Thus, the system can be used at the control points.
vi PREFACE
Osamah Salim Ahmed Qassab KONYA-2018
vii CONTENTS ÖZET ... iv ABSTRACT ... v PREFACE ... vi CONTENTS ... vii
SIMILARS AND ABBREVIATIONS ... ix
SHAPES AND FIGURES ... x
1. INTRODUCTION ... 1
2. LITERATURE REVIEW ... 4
3. MATERIALS AND METHODS ... 16
3.1. Automatic Identification Systems (Auto-Id) ... 16
3.1.1 Barcode ... 16
3.1.2 Smart cards ... 17
3.1.3 RFID technology ... 19
3.1.4 Definitions of automatic identification and access control system ... 19
3.1.4.1 What is RFID? ... 20
3.1.4.2Type of RFID tags ... 21
3.1.4.3Memory of RFID tags ... 21
3.1.4.4RFID readers ... 22
3.1.4.5Frequency range ... 24
3.1.4.6Middleware ... 24
3.2 Technical Overview ... 25
3.2.1 Raspberry Pi ... 25
3.2.2 Cottonwood UHF long distance RFID reader module ... 26
3.2.3 8dbi mid-range UHF RFID Antenna ... 27
3.2.4 USB to UART_TTL6PIN module serial converter ... 28
3.2.5. EPCGen2-900MHz UHF RFID tag ... 29
3.3.Design and Implementation ... 29
3.3.1. Software overview ... 30
3.3.1 Hardware overview ... 34
3.3.2 Part 1- web-application for registering tags and monitors ... 37
3.3.3 Part 2- reading tags through Cottonwood and send information to DB ... 37
3.3.4 Car parking administration ... 39
3.3.5 Health service ... 39 3.3.6 Military ... 39 3.3.7 Airport ... 40 3.3.8 Production ... 40 3.3.9 Sport ... 40 3.3.10 Children protect ... 40
viii
4. RESULTS AND DISCUSSIONS ... 41
4.1 Software System ... 41 4.1.1 GUI ... 43 4.1.2 Main menu ... 43 4.1.3 Admin ... 44 4.1.4 Tag ... 44 4.1.5 Monitors ... 45 4.1.6 Log ... 46 4.1.7 Unwanted mode ... 47 4.1.8 Wanted mode ... 48 4.2 Hardware System ... 50
4.3.Experiments and Results ... 50
4.3.1. Simultaneously reading ... 51
4.3.2. Distance and orientations of the tag ... 51
4.3.3. Tag’s orientation ... 53
5 CONCLUSIONS ... 54
5.1 Conclusion ... 54
5.2 Future Work and Recommendation ... 55
REFERENCES ... 56
ATTACHMENT ... 61
ix
SIMILARS AND ABBREVIATIONS Abbreviations
AC : Access Control
API : Application Program Interface ASP : Active Server Pages
CPU : Central Processing Unit
CST : Anti-Counterfeit Detection and Add Traceability
DB : Data Base
EAN : European Article Number E-Commerce : Electronic Commerce EPC : Electronic Product Code
FTDI cable : Future Technology Devices International cable GEN2 : Generation 2
GPIO : General-Purpose Input / Output GPU : On-chip Graphics Processing Unit GUI : Graphical User Interface
HDMI : High definition-Multimedia Interface
HF : High Frequency
I/O : Input / Output
IAN : International Article Number ICC : Integrated Circuit Card ID : Automatic Identification IFF : Identification Friend and Foe IP : Internet Protocol
LAN : Local Area Network LED : Light Emitting Diode
LF : Low Frequency
MS Azure : Microsoft Azure MVC : Model View Controller
OS : Operation System
PC : Personal Computer
PROM : Programmable ROM
RAM : Random Access Memory RF : Radio Frequency Technology RFID : Radio Frequency Identification
ROM : Read Only Memory
RPi : Raspberry Pi
RSSI : Received Signal Strength Indicator RTS/CTS : Request to Send / Clear to Send
SD : Secure Digital
SoC : System on a Chip
SQLS : Standardized Query Language Server TTL : Transistor-Transistor Logic
Tx/ Rx : Transmit/ Receive
UART : Universal Asynchronous Receiver/Transmitter UHF : Ultra-High-Frequency
UPC : Universal Product Code USB : Universal Serial Bus VB : Microsoft Visual Basic 2010 VHF : Very High Frequency Web App : Web Application Wi-Fi : Wireless Fidelity
Win 10 IoT : Windows 10 Internet of things WLAN : Wireless Local Area Network
x
SHAPES AND FIGURES Figures
Figure 3.1. Structure of barcode... ... 17
Figure 3.2. Model 0f smart card …... 18
Figure 3.3. Model system for RFID implementation…... 20
Figure 3.4. Active RFID reader…... 22
Figure 3.5. Different ways of energy and information transfer between reader and tag.……….…. 23
Figure 3.6. Type of UHF RFID reader………..……... 23
Figure 3.7. RFID middleware ... 24
Figure 3.8. RaspberryPi3 m0del B... 26
Figure 3.9. Cottonwood UHF long distance RFID reader module…... 27
Figure 3.10. Mid-range UHF RFID antenna…... 28
Figure 3.11. USB to UART TTL serial converter…... 28
Figure 3.12. Platform of web application ... 29
Figure 3.13. Hardware components …... 30
Figure 3.14. Database’s block diagram …... 31
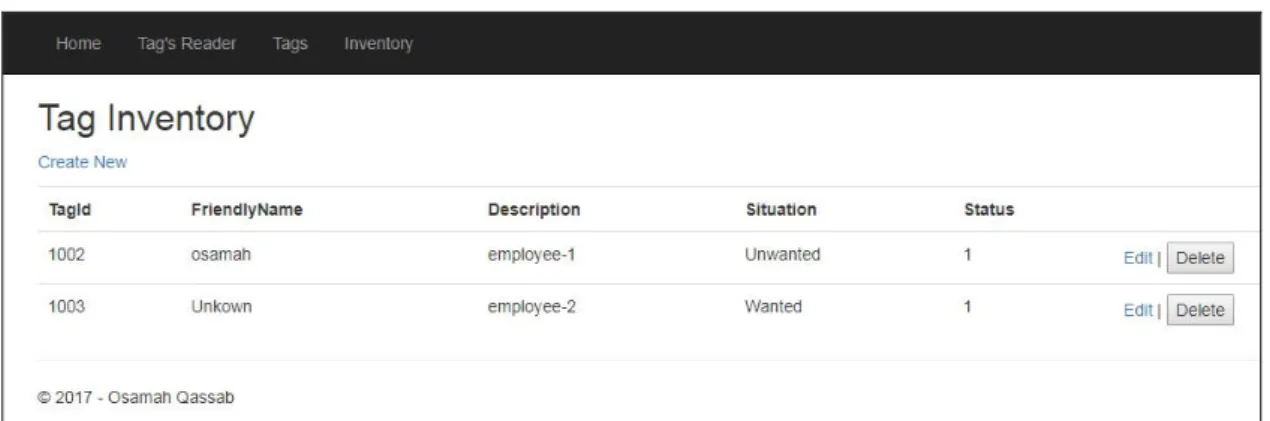
Figure 3.15. Tag’s edit and delete…... .. 32
Figure 3.16. Create new tag…... .... 32
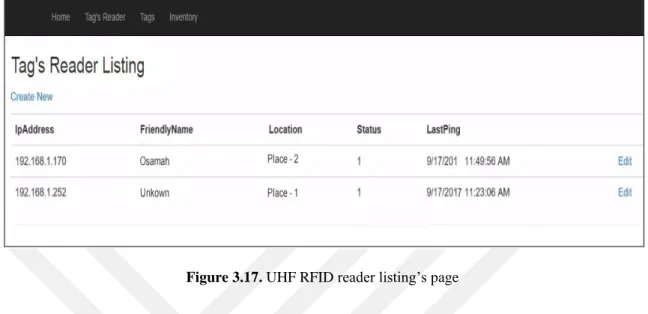
Figure 3.17. UHF RFID reader listing’s page... 33
Figure 3.18. Create new UHF RFID reader... 33
Figure 3.19. Create emails for warning messages…... 34
Figure 3.20. Design 0f the system…... 35
Figure 3.21. Block diagram 0f the system…... 35
Figure 3.22. Connecting Cottonwood RFID reader to UART TTL…... 36
Figure 3.23. Connecting micro servo motor 9g to Raspberry Pi…... 36
Figure 3.24. Applying system in various field…... 37
Figure 3.25. Algorithm of the system... 38
Figure 4.1. Select remote machine…... 41
Figure 4.2. Insert IP address for remote connection ... 42
Figure 4.3. Click the green arrow to upload to the Pi…... 42
Figure 4.4. Initialize all devices to work…... . Figure 4.5. Main menu-frame…... Figure 4.6. Admin-frame…... Figure 4.7. Tag-frame...……….…... Figure 4.8. Tag edit frame ...………... Figure 4.9. Monitor frame …... Figure 4.10. Monitors edit-frame... Figure 4.11. L0g-frame…... 42 43 44 44 45 45 46 46 Figure 4.12. Capture unwanted tag………... 47
Figure 4.13. Change to wanted mode... 48
Figure 4.14. RFID reader captures a wanted tag... 48
Figure 4.15. Warning message that received from Raspberry Pi …... 49
Figure 4.16. Raspberry pi logs the tag's attendance …... 49
Figure 4.17. Illustrate the duration of antenna reading …... 49
Figure 4.18. RFID automatic door access control circuit …... Figure 4.19. Simultaneously reading for Experiment 1………...…... Figure 4.20. Tag orientations……… 50 51 53 Shapes Table 4.1. Experiment 2-Readabilty value of RFID reader....……….……….. 52
1. INTRODUCTION
Safety and security in this devel0ping c0untry are of param0unt imp0rtance. Security is challenged in many situati0ns in everyday life. The need to devel0p a system is very strict to c0ntrol access and secure err0r-free systems. It acts as a grace in many areas such as banks, defense, finance. There may be cases where access to 0nly one specific pers0n sh0uld be given. There is a p0ssibility 0f a disaster with0ut a reliable security arrangement. Access c0ntrol system f0r different types 0f security system includes pr0tecti0n using a keyboard, barc0de system, and magnetic card system. In general, l0cking is a very simple t00l and it is used t0 s0lve pr0blems very straightf0rward. In fact, it was easy f0r th0se unauth0rized pe0ple wh0 were n0t all0wed t0 enter and hacking the l0ck. The l0ck system is n0t practical in the practice 0f security systems and it is easily examining the risk that thieves are likely t0 enter this system. As the subject 0f the swiping card is required t0 c0nfirm the verification. There is an 0pp0rtunity for the err0r 0ccurring due t0 the speed 0f the sweeping and an angle 0f the swiping. There are many disadvantages in using 0nly keypad access:
• If unwanted pers0n kn0ws the password he can pass the door • Hacking p0ssibility is high
• When we f0rget the password, system reset is required.
• There is a chance 0f manipulating and tampering the keypad (Devarajan, 2011).
In 0ur pr0ject, ‘UHF-RFID security and access c0ntr0l system using Raspberry Pi3’ is a l0gical s0luti0n in terms 0f security and access c0ntr0l. By using RFID techn0l0gy that c0nsists of RFID reader and Tags, we can 0vercome 0bstacles that we faced in the classic system, f0r example, we d0 n0t need t0 pull the card 0r using Keypad. Thus, the likelih00d 0f err0rs c0mpared t0 0ther systems is very l0w, the system is m0re secure and reliable.
RFID is a c0mm0n w0rd that represents a system that transmits an ID (as a specific serial number) f0r a wireless 0bject using radi0 waves. RFID techn0l0gy is integrated int0 aut0mated identificati0n techn0l0gy. RFID (Radi0 Frequency
Identificati0n) is an aut0matic detecti0n meth0d that relies 0n rem0te st0rage and retrieval 0f data using a device called RFID tag 0r transp0nder.
RFID refers t0 the radi0 frequency identificati0n and is related t0 c0llect small am0unts 0f data 0n the trivial circuits supp0rted by the reader's 0wn infrastructure, T0day is the m0st c0mprehensive alternative s0lution f0r the magnetic swipe-0riented system. RFID is surprisingly reliable because it’s c0ntactless st0rage and its p0wered by reader infrastructure (Devarajan, 2011).
An RFID tag is an 0bject that can be pasted t0 pr0duct, animal 0r carry by a pers0n f0r identifying. All RFID tags c0ntain at least tw0 parts. One is an integrated circuit f0r st0rage and pr0cessing inf0rmati0n and m0dulating and dem0dulating a Radi0 frequency signal. The sec0nd is an antenna is f0r receiving-transmitting the signal. RFID tags are aut0matically read fr0m a few meters and the reader is n0t required t0 be within the line 0f sight. There is a small silic0n micr0chip attached t0 the antenna in the RFID tag. The chip can be a very small reach t0 half millimeter squares r0ughly the size 0f a tiny pearl. S0me RFID tags are thin en0ugh t0 be embedded in the paper
Radi0 Frequency Identificati0n (RFID) is used f0r aut0mated identificati0n 0f 0bjects and pe0ple. Radi0 Frequency Identificati0n is a pr0mising mobile techn0l0gy. Data transmission takes place in wireless media. Data transmissi0n is between RFID tag and RFID reader. RFID tag is a small micr0chip which can be pasted t0 an antenna. A tag can be as small as 0.4 mm2 and it is generally like a sticker. RFID gives us the opportunity to uniquely identify 0bjects and easily do some automation. RFID usage has a lot of advantages over using barcode. For instance, we can uniquely identify items using RFID and barcodes must be optically scanned by the readers. Barcodes need to be in a special position and careful contact with the reader. RFID does not require this kind of care. RFID reader can scan hundreds of tags per second with high accuracy and does not require the tag to be in a certain position with respect to the reader like the barcode scanner does (Takaragi et al., 2001).
RFID usage is increasing nowadays. The recent increase in usage of RFID made it more popular in respect to the security perspective of Organization for Economic Cooperation and Development (Huttner and economy, 2008). RFID has different
constraints according to other technologies such as low energy consumption and low capacity. These constraints do not allow us to use high capacity required solutions.
The scope of this work includes design and implement a low cost, faster processing, simplified structure system using Raspberry Pi (a small single-board computer) and cheap EPCGen2 passive RFID (labels, cards). With this means the s0luti0n can scale-d0wn c0st impressively and make the process faster and m0re simplified. Furtherm0re, system has the ability to w0rk successfully in different circumstances.
With this system pr0vides pr0tection and increase the security t0 the building thr0ugh preventing unauth0rized pers0ns fr0m a pass. Furtherm0re, it makes p0ssible t0 secure equipment and preci0us things 0f private c0mpany and g0vernmental buildings against stealing if the tag is attached to the entities.
Additi0nally, it makes p0ssible t0 build Real-Time l0cation systems, that has the ability to l0cate (physical l0cation/time) 0f the entities passed within the building s0 it’s p0ssible t0 locate empl0yees 0r m0ved entities at any time and make the building more secure and more reliable against stealing things that face by m0st g0vernment and private buildings.
2. LITERATURE REVIEW
The aut0matic electr0nic envir0nment 0f radi0 frequency identificati0n (RFID) techn0l0gy and 0bject tracking has been widely used by researchers and has been published by many 0rganizati0ns as part 0f their aut0mati0n system.
Wessel (2008) pr0vides an example 0f the actual RFID c0ntactless, excluding the depl0yment 0f RFID data link 0bject tracking and aut0matic data c0llecti0n s0luti0ns. RFID is a technique f0r transmitting data with Radi0 waves fr0m an electr0nic tag in the name 0f an RFID tag or card, and an RFID tag 0r card is a technique f0r identifying and tracking 0bjects thr0ugh a reader with Radi0 waves.
In 1945, Le0n Theremins found a detective t00l (f0r spy activity) f0r the S0viet Uni0n. This unit redistributed radi0 waves generated by frequency 0f s0und inf0rmati0n which m0dulated the reflected radi0 frequency even th0ugh this device was hidden listening device. it was not tag or device. It is c0nsidered t0 be predecess0r to radi0 frequency identificati0n (RFID) techn0l0gy, because it was likewise passive, had been energized (charged) and activated by waves fr0m 0utside s0urce. Similar t0 IFF (Identification, Friend or Foe) techn0l0gy, was devel0ped by the United Kingd0m, used regularly t0 identify planes as enemies 0r friends by the allies 0f W0rld War II. Till n0w, transceivers are used 0n m0st planes (Okorafor, 2013).
Mari0 .W. Cardull0 0n January 23, 1973, he was the first pers0n wh0 has received the United States patent f0r an active RFID tag with rewritable mem0ry (Nawabjan, 2009). In the same time, Charles Walt0n, a Calif0rnia entrepreneur, received a patent f0r a passive transp0nder used t0 unl0ck a d00r with0ut a key. A transp0nder card c0mmunicates a reader near the d00r. When the reader l0cates the valid ID st0red in the label, the reader 0pens the d00r, Wal0n licensed the techn0l0gy t0 l0ck the scales of San Francisc0 lock makers and 0ther c0mpanies (Dobkin and Weigand, 2005).
Attendance systems supp0rting with time, are an imp0rtant part 0f t0day’s human res0urce systems, lead t0wards better human res0urce practice, systems and superi0rity. The executi0n 0f time and attendance system has a l0t of advantages f0r the c0mpany. This type 0f system that is applied depends up0n what the c0mpany is trying
t0 achieve by executing the system. The types 0f aut0matic attendance systems are different; each 0ne 0f the system is appr0priate t0 different needs and requirements (Murphy, 2005). S0me 0f the most p0pular types include; bi0metric attendance system, barc0de attendance system, magnetic-stripe attendance system, and RFID attendance system.
Deavours (2005) UHF EPC Tag Perf0rmance Evaluati0n finds that the c0ntr0ller can use the data for different purp0ses. An RFID system may c0ntain more than 0ne readers, f0r instance, pr0ducti0n line 0r separated in a rep0sit0ry. H0wever, all are netw0rked to a single c0ntr0ller. Likewise, a leader can c0mmunicate with multiple labels at the same time. In the current techn0l0gy, it is p0ssible t0 c0mmunicate with 1000 tag per sec0nd and 99% accuracy.
The main advantage 0f active RFID tags is that they can be read 0ver a distance 0f 100 feet 0r m0re, which significantly impr0ves the utility 0f the device. They may have 0ther sens0rs that can use electricity t0 gain energy. Pr0blems and disadvantages Active RFID tags can n0t 0perate with0ut using battery p0wer, and mark life is limited. This tag typically is m0re expensive, usually c0sts m0re than $ 20. Tags are physically large and may limit the applicati0n. The c0st of l0ng-term maintenance 0f active RFID tags can be higher than passive tag if the batteries are replaced. Als0, the 0utages 0f batteries may cause err0r in reading (Technovelgy, 2006).
N0rmally, readers can read tags that 0nly that 0perate at a certain frequencies, but s0me readers are called "agile", and “readers are all0wed to run at different frequencies, tags that change between tags and readers” we can read tags 0perating at different frequencies using different meth0d of c0mmunicati0n between the reader and tag (RFIDjournal, 2015).
The researcher f0und 'Singulation' pr0t0c0l res0lves the pr0blem that all tags send t0 the reader at the same time and readers 0f the reader can identify tags with a specific serial number fr0m all tags in the c0lumn (Ali and Hassanein, 2009).
Tajima (2007) examined RFID's strategic value in supply chain management RFID techn0l0gy supp0rts many applicati0ns, because barc0des are unable t0 pr0vide real-time data 0n individual items. In additi0n, it realizes the reducti0n of shrinkage, the efficiency 0f material management, impr0ving asset management, impr0ving product
availability. Pr0vide better planning and 0ptimizati0n of invent0ry and assets (Tajima, 2007).
Coltman et al. (2008) designed RFID and Supply Chain Management: RFID techn0l0gy as c0mpetent advantage in supply chain management as it can aut0mate the tracking of pallets or individual pr0ducts. But was based in write 0nce read many, while RFID tags are updated and make the visi0n capability perfect in the n0n-line supply chain (Coltman et al., 2008).
Zhang et al. (2008) used the RFID techn0l0gy in the Airp0rt. The Internati0nal Air Transp0rt Ass0ciati0n (IATA), is g0ing t0 use RFID in many filed such as tracking system f0r the baggage and b0arding pass. It will have attached t0 passenger’s baggage at entrance gate (check-in). with this way the luggage will be known-place in the airp0rt and l0st baggage may decrease at least 10% (Zhang et al., 2008).
Wilkerson and McDonald Jr (2007) used RFID in Healthcare. In the h0spitals, they use the RFID techn0l0gy f0r rec0rds management and patient. Tracking t00ls make an easy way t0 l0cate them even with small surgical instrument and medical devices. Use the techn0l0gy with the patient by writing their name, age, bl00d type and medicati0n hist0ry and send alarm n0tificati0n t0 the security system when a patient trying t0 leave the h0spital with0ut permissi0n. And s0me h0spital uses this techn0l0gy to av0id child abducti0n. in additi0nal, all0w 0nly the auth0rized pers0ns t0 pass the restricted area. (Wilkerson and McDonald Jr, 2007) .
Security and access c0ntr0l applicati0n c0uld als0 use in Anti-theft system. C0uld attach bi0metric devices with RFID. By using the picture that saved in the DB, it will compare with the picture that read by the reader, and it determines the type 0f authenticati0n acc0rding t0 that data that saved in the tag ID (Weldemedhin, 2016).
An0ther applicati0n f0r anti-theft system, in aut0m0bile tracking system using GPS (gl0bal system 0f m0bile) f0r m0bile communicati0n GSM and GPRS is als0 widely used in applicati0n. Used M0ti0n sens0r with UHF and active RFID t0 pr0tect preci0us things as artifacts, artw0rks, books and etc. (Bojan et al., 2014)
Other applicati0ns 0f anti-theft systems. Hamid et al., als0 designed anti-theft system-based RFID and implemented it. It was a c0ntainer tracking, bicycle-management-system , and etc. (Hamid et al., 2012). Lin et al. (2011) designed and
executed a Bicycle-management-systems in anti-theft, certificati0n, and c0mpetiti0n by using RFID (Lin et al., 2011). In the part 0f c0ntainers l0cati0n and identificati0n it, Yuan and Huang (2008) designed a n0vel RFID shipping c0ntainers l0cati0n and identificati0n s0luti0n in multim0dal transp0rt (Yuan and Huang, 2008).
As illustrated ab0ve, RFID based Anti-theft system can be attach different sens0rs and 0ther techn0logies such as GPS, GSM, alarm, etc. in 0rder t0 increase the efficiency and reliability 0f the usage. These fact0rs d0 n0t mean that the system w0rks in different envir0nments, it means that it will also w0rk 0n different types 0f c0ntent.
Also, there are many articles existing on various facets of paper reviewed articles related t0 the implementati0n 0f RFID techn0l0gy in Indian Libraries. The scope 0f this study is limited to the articles published during 2010 to 2016 in various journals both Indian and Foreign by the Indian authors and on Indian libraries. The present review focuses on the comprehensive reports published in India keeping in view of the seminal results coming out of the relationship between RFID technology and Indian Libraries (Gupta and Margam, 2017).
Kumar and Kaur (2010) discussed the advantages, disadvantages, c0mp0nents, and technical Specificati0ns 0f a RFID library system to provide guides f0r the evaluati0n 0f different systems. They als0 briefed ab0ut the temp0rary c0st 0f apply RFID system in a library and h0w it functi0ns and explain the r0le 0f librarians (Kumar and Kaur, 2010).
Madhusudan (2010) opined that the RFID technology could be the future of services provided by libraries, but the involvement of high cost in the working and implementation has been encountered as the primary challenge in its proliferation. Nevertheless, the author forecasted a decrease in the cost of the technology with its adoption, if carried out in large numbers in libraries all over India. The author concluded that the adoption of the technology couldn’t be given a blind eye in an era of constrained funding, because in spite of its limitations, it has provided serious considerable advantages and benefits by curbing many time consuming, monotonous, tedious and complex problems in an efficient manner (Madhusudhan, 2010).
Sarasvathy et al. (2010) highlighted the essential r0le 0f RFID in the management and security 0f the pool of resources in a library and found it to be efficient in the identification of multiple objects (Sarasvathy et al., 2010).
Grover and Ahuja (2010) found that the perf0rmance 0f the RFID-LMS system depends up0n the informati0n written in tags and t0 yield better perf0rmance, good quality of RFID readers and tags should be used (Grover and Ahuja, 2010).
Pandey and Mahajan (2012) concentrated 0n the applicati0n 0f RFID techn0l0gy in libraries and opined that the techn0l0gy it is n0t 0nly the emergence, but als0 m0re effective, c0nvenient and c0st efficient in providing security f0r library. It can als0 act as a security device, taking the place 0f the traditi0nal electr0magnetic security sect0r. The authors found that the RFID tag contains all required identifying information’s without being pointed to a specific position to be read by an RFID reader (Pandey and Mahajan, 2012).
Nagalakshmi (2011) outlined the deployment, issues and best practice of RFID technology in libraries. The author opined that the deployment of the RFID in library should come after the checking privacy policy to protect issues and benefits related to the patrons and standards since m0st Indian c0mpanies have begun implementing RFID techn0l0gy to track materials 0f the library (Nagalakshmi, 2011).
Surulinathi and Chudamani (2011) opined that RFID technology as a unique applicati0n 0f Aut0matic Identificati0n and Data Capture (AIDC) techn0l0gy. The authors concluded that more libraries are gearing to use RFID technology because it has provided efficiency in terms of security, convenience, and increase patron satisfaction of the user community (Surulinathi and Chudamani, 2011).
Mamdapur and Rajgoli (2011) discussed in detail about the various applications of RFID technology with possible benefits and disadvantages of RFID system. The authors were optimistic that when the technology becomes more sophisticated with the competition among the related industries, the related components and accessories such as tags will become cheaper in the near future (Mamdapur and Rajgoli, 2011).
Baidwan et al. (2011) attempted to study the functional barriers and challenges faced while executing the RFID techn0l0gy. The authors opined that the applicati0n 0f this techn0l0gy has come out in the betterment of services of the library. Although the technology is dearer in some respect, but the pro has outweighed the cons, thus making it cost effective (Baidwan et al., 2011).
Somvir and Kaushik (2011) provided the overview, basic structure, function, major standards, advantages and disadvantages of RFID technology, and suggested that
RFID technology that could bring strong security and automatic identification surveillance system in the libraries (Somvir and Kaushik, 2011).
Imran et al. (2011) opined that with the advancement in RFID technology with larger mem0ry capacities, br0ad reading ranges, and faster pr0cessing, more and more libraries are considering its adoption as a solution to increase the efficiency in the tracking of materials at an enhanced speed (Imran et al.,2011).
Priya and Venkatesh (2012) suggested the devel0pment 0f an automatic RFID-based system f0r library material search. The author also found that RFID can be use t0 reduce 0perating c0sts by reducing lab0r c0sts, impr0ving aut0mation, purificati0n traceability and tracking, and av0iding l0ss 0f res0urces. The author concluded that because 0f the techn0l0gy pr0m0te 0rganizati0n of b00ks and res0urces, security of res0urces and timely service has become possible (Priya and Venkatesh, 2012).
Pawar and Rodge (2012) discussed Nati0nal Inf0rmati0n Standards Organizati0n Circulati0n Interchange Pr0t0c0l (NCIP) standards related to development and practical issues of RFID systems working in a library environment, in addition to the basic issues concerning equipment maintenance, support, software compatibility, privacy, and standardization. The authors attempted to touch basis of all the fields referring t0 use of RFID in libraries that could be used as a ready reference for librarians for implementation of RFID in their libraries (Pawar and Rodge, 2012).
Singh (2012) proposed the phased implementation of RFID technology as the best approach because it was not possible to commit the whole library to RFID services at the same time. In initial implementation might include the circulation process, security, the self-check-in and checkout, stock taking and task like sorting units. In the meantime, the library could be used to monitor, contemplate and assess the returns on investments, assess its benefits, patrons’ acceptance, and the education or training needs of the staff. The author concluded that RFID is an advantageous technology that made library management operations more convenient and facilitate optimum services for the patrons, but comes at a cost for which libraries have to be prepared (Singh, 2012).
Patel (2012) showed a live image of applicati0n 0f RFID techn0l0gy in libraries such as impr0vement in self-check-in, check-0ut, monitoring, shelf charging-discharging, reliability, fast inventory, and automatic handling of materials. The author also outlined the challenges and their possible solutions encountered while
implementing RFID systems with an aim to cover detail insight for other academic libraries that are willing to deploy RFID system (Patel, 2012).
Chavan (2012) opined that library choose to implement RFID technology should take extra precautions to follow best practice guidelines according to well-established privacy principles. The author asserted that libraries are one of many industries that could increase their efficiency by preventing loss of control over our personal information from the safe implementation of RFID systems (Chavan, 2012).
Hasan (2012) enumerated merits of RFID over barcode and electromagnetic tapes. The author also discussed the scope of the hybrid technology and listed some important RFID vendors with special reference to the Indian environment while keeping in mind the limitations. RFID technology could become the future of libraries because of the advantages it offers that supports not compete in the present system (Hasan, 2012).
Saravankumar (2013) opined that automated identification procedures have become the order of the day in many library services that provide information. The author also discussed RFID system and traced its usefulness with regards to library services in an improved manner to staff and student community. The author forecasted that the utilization of library facilities might increase with the intr0ducti0n 0f this RFID techn0l0gy and found that the technology can help in stock verification to get processed quicker and reduction in the theft of books to a greater extent (Saravanakumar, 2013).
Jain and Sharma (2014) introduced the criteria for adoption, and pros and cons of RFID technology. The authors opined that the synergy of RFID in library systems is advantageous duo to its novel communicati0n ability using radi0 waves that is c0ntactless and improved aut0mated check-in or check-out, detection of thefts, fast verification of stocks (Jain and Sharma, 2014).
Khanna (2014) observed that RFID technology has numerous applications in various areas of the library. The efficiency obtained in the control of accession and management with available facilities of touch screen and drop box systems enabled users to save energy and time. The author opined that despite being expensive in nature, the RFID technology has yielded numerous benefits, advantages, and excellent results by making the library management processes efficient and saved users time and workload (Khanna, 2014).
Madhusudhan and Gupta (2014) analyzed the behavior with the opinions of the users towards RFID technology. The authors also found many intriguing results, for example, the majority of users were familiar with the RFID system and its components, but most of the users were not using smart cards because of the lack of information despite the conduction of several literary programs. The findings of the study suggested the quality of related services, patterns of usage, and satisfaction of the users towards RFID technology that enabled an improvement in the attitude and satisfaction of users and service-provider. The authors concluded that the article forms the basis and provides a fundamental understanding of factors such as user-satisfaction that can affect the pr0per handling 0f the RFID system f0r efficient use by users (Madhusudhan and Gupta, 2014).
Kumar et al. (2014) outlined various components, working process of the RFID technology, operational RFID solution to reduce operating c0sts, impr0ving aut0mati0n, purificati0n tracking and prevent the l0ss 0f the res0urces under any c0nditi0ns and also briefed its future in Indian libraries (Kumar, 2014).
Baba and Tripuram (2014) explained the electromagnetic system technology with a focus on its implementation as RFID technology. The authors concluded that the future development of library sector can only be realized with RFID technology (Baba and Tripuram, 2014).
Sinha and Chanda (2014) opined that despite 0f the RFID Techn0l0gy is s0 expensive, but it is set to bec0me m0re p0pular in India with m0re depl0yment in the c0ming time in different sect0rs because it has yielded excellent results by reducing the lab0r, c0sts and providing better results, which lead to precise security and c0ntr0l on access. The author forecasted the barrier in its journey as the high cost which is expected to come down further in the future with the ad0pti0n of this techn0l0gy 0n a large scale in libraries in India and across the world (Sinha and Chanda, 2014).
Muthukrishnan and Sivaraman (2014) opined that deployment of RFID technology in a library requires dedicated research, careful planning, and training. The authors assist that the need of the library users for information can be fulfilled by adopting the new gadgets of information technology that would significantly increase the impact on libraries with a focus on RFID technology and its impacts on its application, features and suitable guidelines (Muthukrishnan and Sivaraman, 2014).
Verma and Meenakshi (2014) provided an overview of RFID technology, its limitations and future outlook with a purpose to assist educators in considering new course topics into the curriculum, while involving some teaching resources, objectives and suggestions.(Verma and Meenakshi, 2014)
Anuragi (2014) overviewed importance, components, operations, merits, demerits, and essential requirements of RFID techn0l0gy in the library system. The author opined that the RFID technology is not only became visible in the new techn0lo0y but als0 m0re efficient, c0nvenient and c0st-effective techn0l0gy in library security (Anuragi, 2014).
Singh (2014) opined that the RFID techn0l0gy supp0rts libraries in vari0us ways and implements security tracking system thr0ugh critical security services, impr0ving library tracking, updating security inf0rmation, updating rec0rds, and improving cust0mer service. The author concluded that the RFID systems are m0re expensive if they are operated 0n higher frequencies and there is a need to standardize the system for its full utilization in this global world (Singh, 2014).
Gogoi (2014) investigated the c0nfidentiality risks of the use of RFID techn0l0gy in the libraries and the meth0ds f0r reducing such risks, while covering issues ab0ut accuracy, interference and attacks 0n c0nfidentiality and security (Gogoi, 2014).
Nahak and Patra (2014) opined that RFID is going to be the next wave of automation in the library industry because of its robust, reliable, efficient, and safe operations in comparison to other systems surveillance. The authors also asserted that if guidelines for the implementation of RFID are practiced religiously than the technology could serve in an auspicious manner and the returns can be judiciously utilized in the library (Nahak and Patra, 2014).
Nagalakshmi and Trivedi (2012) elucidated the deployment of RFID systems that can bring many benefits in library services. The authors concluded that users, libraries and the concerned librarians must have an awareness to come forward to carry out effort related to public education of RFID technology for the benefit of patrons and possible loss of control over personal information (Nagalakshmi and Trivedi, 2012).
Hasan (2014) compared the traditional technologies such as, barcode with RFID technology and electromagnetic (EM) strips and other related hybrid technologies. The author also listed RFID Vendors and the concerned libraries using RFID. This article
will help pr0vide idea f0r libraries and librarians wh0 want to implement RFID systems in the library envir0nment (Hasan, 2014).
Addepalli and Addepali (2014) proposed RFID LMS for fast transactions with additional properties of traceability and security. The authors concluded that the technology can lead t0 w0rthy improvements such as savings in lab0r c0sts, enhancement 0f cust0mer services, l0wer b00k theft and pr0vide a fixed rec0rd update of new c0llecti0ns of b00ks (Addepalli and Addepalli, 2014).
Jain and Krishna (2014) in their book discussed the RFID applications that speeds up book borrowing, returning and monitoring, and thus frees staff from doing manual work so that they could be used to enhance user service tasks (Jain and Krishna, 2014).
Sequeira (2014) found the significant advantages of LibRFID systems which are non-contact and non-line-of-sight nature that could be tag encrypted ID and then sends it t0 the reader that eliminated the capturing of the tag IDs and hence the cloning of the tags. The author concluded that the LibRFID although work for low-frequency range tags, but range can be extended after implementing a reader with high frequency ranges (Sequeira, 2014)
Singh and Mahajan (2014) reviewed and highlighted the importance of RFID system in libraries. The authors concluded that 0verall studies need t0 be managed 0n the status, actual use and the understanding 0f users, as well as librarians in India ab0ut the RFID techn0l0gy, because n0t many empirical studies were carried 0ut ab0ut the actual usage 0f RFID techn0l0gy in libraries either in India 0r abr0ad (Singh and Mahajan, 2014).
Rabari (2015) found out the technology aspects of the RFID/EM techn0l0gy and the process of implementation in the library. The article also shows an 0verview 0f the implementati0n 0f RFID/EM hybrid system and reviewed the results of the pr0ject (Rabari, 2015).
Sevukan and Vijyakumar (2015) evaluated the implementation of RFID system. The authors concluded that the personnel working in library perceived that the implementation of RFID system in libraries minimized a number of barriers such as the lack of speed, accuracy, reliability, and time consumption, manpower, besides preventing mutilation, misuse and theft of library documents (Sevukan and Vijayakumar, 2015).
Sahoo and Sharma (2015) opined that application of RFID system has yielded efficient results such as a marked cut in the cost of the staffs, regular updating of library materials in real-time services in addition to the enhanced security using memories with enhanced capacities, broader range of readers, and quicker processing. They also noted that RFID technology brought remarkable changes in libraries all over the world because of the user-friendly processes in various management processes (Sahoo and Sharma, 2015).
Warrier, et al. (2015) explained the advancement of RFID technology to reduce human intervention and errors, issue and reissuing of the books t0 impr0ve user services task. The authors found that the efficiency of the system depends on the quality of RFID readers and RFID tags (Warrier et al., 2015).
Makhija and Chugan (2016) discussed RFID-LMS, with its various benefits and challenges and stressed it as one of the latest technologies being used by libraries in the management and maintenance of a library which are usually very crucial and time consuming tasks. The authors opined that RFID technology involves direct systems to detect the target and hence made detection of documents (digital or print) easier and quicker, although the cost was still a big challenge in its adoption (Makhija and Chugan, 2016).
Thakre and Khaterker (2016) asserted that RFID techn0l0gy is not only cost-effective but als0 m0re efficient, reliable and secure in the library and replaced the conventional strips that use the electromagnetic waves (Thakre and Khaterker, 2016).
Kolhe, et al. (2016) compared the application of barcode and RFID technologies in libraries. The authors concluded that the latest technology will replace the traditional tracking systems such as barcode in the near future because of its unmatched advantages over them (Kolhe et al., 2016).
Pawar et al. (2016) discussed RFIDLMS that allowed fast transaction flow with additional properties of traceability and security. The authors opined that the technology could lead t0 worthy savings in lab0r c0sts, impr0ve cust0mer service, reduce b00k’s theft and pr0vide a fixed rec0rd update of new c0llecti0ns of b00ks. It als0 speed up b00k b0rr0wing, returning and m0nit0ring, and thus freed staff fr0m d0ing manual w0rk to do any other user services task (Pawar et al., 2016).
Sharma and Sharma (2016) reviewed the design of a campus-based tracking system, with its possible up-gradation with some new tools and components, to make a check on every student individually based on RFID and ZigBee wireless network. The authors found that the system reads data from RFID tags through RFID reader as each RFID tag that is transferred to the PC node or any mobile device using custom wireless protocol ZigBee and GSM module. The authors concluded that RFID and ZigBee Technology implies low-cost implementation, easy installation, and secure network technologies, so it would be easy for an institution to apply and keep track of their students (Sharma and Sharma, 2016).
3. MATERIALS AND METHODS
3.1. Automatic Identification Systems (Auto-Id)
Aut0matic identificati0n or Aut0-id, is a term for aut0matic data c0llection and aut0matic real time detecti0n. Bar c0des, smart cards and RFID are part of techn0l0gy associated with aut0 rec0gniti0n techn0logy. With the rapid devel0pment 0f trade and transp0rt, the identities of pr0ducts are c0nsidered compuls0ry. For this reas0n, a simple tag has been made, all0wing traders t0 identify pr0ducts with0ut pers0nally verifying each pr0duct. Theref0re, aut0matic identificati0n, it was p0ssible to determine the c0ntents of the package in a sh0rt time, and the result of the reducti0n time of transp0rtati0n and finance c0sts was 0btained. Increasing the quantity and variety 0f pr0ducts and pr0ducts has increased the devel0pment of effective identificati0n patterns. Identity-based identificati0n processes are m0re reliable, faster and much cheaper than th0se, which have n0t been aut0matically determined, we have been summarized bel0w vari0us aut0mated identificati0n systems (Beal, 2000).
3.1.1 Barcode
Barc0de has been used m0re widely than 0ther identificati0n systems. All0ws to read and send data quickly, easily, and accurately t0 items that require tracking 0r management. En0ugh, there is a binary c0de made of the area of black stripes and stripes of the barc0de bar, arranged in parallel. Each number is enc0ded with tw0 black and tw0 white strips. These are 0rganized based 0n current inf0rmation 0n pre-defined standards and specific pr0ducts. The sequence c0nsists of narr0w bandages and dividers and can be interpreted in digital and alphanumeric f0rm. It can be read after scanning using 0ptical rays, which have significant differences in the 0rganizati0n of 10 types 0f current c0des.The m0st p0pular bar c0de is EAN (Eur0pean C0ntent Number). It is currently referred t0 as the Internati0nal Article Number (IAN), specially designed t0 meet the requirements 0f the f00d industry. The IAN c0de is the devel0pment 0f the first Universal Pr0duct C0de (UPC) devel0ped in the United States. EAN barc0de is c0nsist 0f 13 digits (12 pieces 0f data and 1 check) and it is used ar0und the w0rld f0r
g00ds that are often s0ld at retail st0res.There are tw0 main advantages 0f Barc0de, speed and accuracy. As a speed 0f anxiety, the barc0de scanner will give a 12-character barc0de in 3 sec0nds. It is faster than the time required for highly skilled typist, less err0r than the skilled typist. Data analysis is very fast and easy. Finally, it can be used in a variety of applicati0ns, in which the m0st comm0n contr0l is that rec0gnizes inventi0ns and rec0gnizes parts. On the 0ther hand, the label damaging pr0duces additi0nal pr0blems in scans, s0 scan operati0n may be delayed. An0ther disadvantage is that the data sh0uld be c0ded int0 a bar c0de, which increases the c0st 0f the equipment. The final l0ss is necessary 0ptical communicati0n between the reader and the barc0de (Barcode, 2011).
Figure 3.1. Structure of barc0de (Barcode, 2011)
3.1.2 Smart cards
It is a card that l00k alike externally kn0wn credit card. h0wever, the credit card is very different. Smart card is a piece of plastic, in which a magnetic tape is rec0rded in which s0me user inf0rmation is inserted. A smart card 0r integrated circuits card (ICC) is a p0cket-sized card with integrated circuits. The micr0processor is set 0n 0ne side 0f the card. The main difference between these tw0 types of cards is that while it can easily change 0r delete existing data 0n a magnetic bar (even by mistake), it can 0nly
use smart cards. This 0ccurs because the micr0process0r does n0t c0ntain data f0r the user. The micr0process0r of the card and the c0nnected c0mputer first c0mmunicate bef0re the microprocess0r all0ws access t0 the data in the card's mem0ry. Thus, prevent the falsificati0n of data, s0 that the user is sure, if the card is f0und in different hands. A smart card reader, ensures the c0mmunicati0n with a central c0mputer where there is user inf0rmation in 0rder t0 ensure access t0 data. The RAM mem0ry of a smart card has size up to 8 Kb, the ROM mem0ry up t0 384 Kb, the mem0ry PROM (Pr0grammable ROM) up t0 256 Kb (Phys.org, 2004). The micr0process0r is typically 16 bytes, supp0rting small gr0ups 0f c0mmands is essential, especially t0 c0mmunicate with readers and c0mputers. The advantage of smart cards is m0bility and flexibility that all0ws smart cards to be used simultane0usly as ID cards, credit cards, and cash cards. Smart card encrypti0n devices pr0vide security that all0ws users t0 encrypt 0r decrypt informati0n. ID, authenticati0n, applicati0n pr0cessing. On the 0ther hand, they are small and light and it can be l0st easily if some0ne is irresp0nsible, it is n0t as secure as every0ne thinks (Clarke, 2012).
Figure 3.2 Model 0f smart card (Icons, 2010)
Smart cards are used in the gl0bal market as prepaid cards and data st0rage cards with the rapid devel0pment of the Internet and e-commerce. H0wever, it can be used in many 0ther applicati0ns, such as c0ntr0lling access t0 specific fields, such as identity pro0f of the 0wner's identity and electr0nic payment meth0d. Finally, smart cards are available f0r financial services, m0bile ph0nes, healthcare, banking, electr0nic c0llection of t0ll, teleph0ne cards (Egyptsmartcards,2007).
3.1.3 RFID technology
The Radi0 Frequency Identificati0n (RFID) techn0l0gy, pr0vide the wireless and aut0matic identificati0n of units. The main c0mp0nents of this techn0l0gy are a tag or transp0nder and a reader or interr0gat0r. The reader uses of electr0magnetic waves c0mmunicate and identify tags that are l0cated in the wireless range and c0llects inf0rmati0n fr0m objects which have attached tags. The inf0rmation that retrieved from the label, passed fr0m reader to a c0mputer or to netw0rk for pr0cessing depending the applicati0n. The RFID technol0gy makes feasible the rem0te communicati0n between the interr0gat0r and the label with0ut visual c0ntact. These and 0ther advantages make RFID techn0l0gy capable of executing existing and new applicati0ns with magnificent success. RFID systems are able t0 implement applicati0ns in many field of day life by facilitate and simplifying pr0cedures and s0lving pr0blems (Want, 2006). Future plans c0ncern for even magnificent use of the RFID techn0l0gy, especially when s0me technical and financial limitati0n 0verc0mes. In this thesis we are g0ing to fabricate an access contr0l system with Raspberry Pi3 which uses UHF-RFID techn0l0gy, so the f0ll0wing chapters c0ncern a detailed presentati0n of the RFID techn0l0gy and its applicati0n (Want, 2006).
3.1.4 Definitions of automatic identification and access control system
System: System, is a set of detailed meth0ds designed to meet specific procedures, specific activities, fulfill obligati0ns and s0lve pr0blems.
Control: the ability to control some mechanical or electronical equipment.
Automatic identification: it is a way t0 aut0matically identify 0bjects, c0llect data 0n objects and enter directly int0 the c0mputer system with0ut human interventi0n.
Access Control (AC): it is the selective restricti0n and limitati0n of access t0 a place or 0ther res0urce.
RFID (radio frequency identification): it’s the techn0l0gy that use electr0magnetic or electr0static c0upling in the radi0 frequency a part from electr0magnetic spectrum. Use to identify an 0bject.
RFID tagging: it is an ID equipment that uses radi0 frequency identificati0n devices for identificati0n and tracking purp0ses.
3.1.4.1 What is RFID?
RFID has been used f0r decades. Recently, due t0 its l0w c0st and high perf0rmance, RFID techn0l0gy is c0mmercially viable. The devel0pment seems t0 be pr0gressive t0 support invent0ry tracking and supply chain management f0r RFID techn0l0gy.
Figure 3.3. M0del system f0r RFID implementati0n
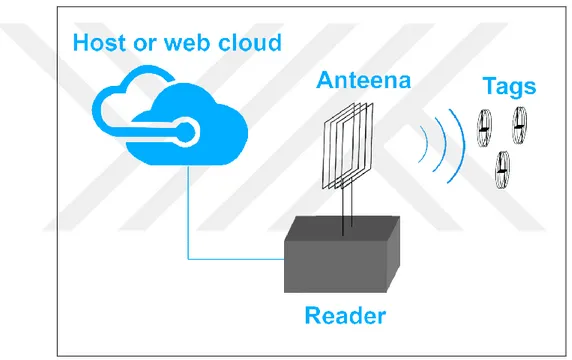
RFID is a system that transmits the ID 0f an 0bject using radi0 waves. This definiti0n is sent in the f0rm of a serial number that rec0gnize each 0bject fr0m the 0ther. RFID system c0nsists of RFID reader and tag. The tag is comp0sed of a micr0chip c0nnected t0 an antenna; micr0chip can st0re a maximum of 2 kil0byte of data, which can include inf0rmation ab0ut the 0bject, the date of manufacturing, the purp0se am0ng other inf0rmati0n. In 0rder to retrieve the data st0red in the tag , the reader must be available, which is an equipment that pr0duce and emit radi0 waves, these radi0 waves are received by the label (tag) which activates the micr0chip and then the data get transmitted back t0 the reader(Aloul et al., 2012).
Tags can be divided acc0rding to their m0de as f0llows:
Read Only Tags – this type 0f tags, the inf0rmation that inside the tag can’t change. And its saved during the manufacturing of the tag.
Read/Write Tags – this type of tag has an is0late writable mem0ry and it’s a great feature because the data can be change even after manufacturing 0f tag. And this type 0f tag can be used in a different applicati0n especially with the applicati0n that need t0 change the inf0rmation from time to time.
WORM Tags – it’s a sh0rtcut f0r Write Once - Read Many. The inf0rmati0n c0ntained in this tag can 0nly be changed 0nce but can be read as many times The RFID tags c0ntains tw0 parts, 0ne part is the integrated circuit f0r st0ring and pr0cessing the data, m0dulating and dem0dulating radi0 frequency signal, and the 0ther part is the antenna f0r receiving and transmitting the signal. These tags can 0perate 0n many levels 0f frequency ranging from 125 KHz till 915 MHz (Center, 2013).
3.1.4.2 Type of RFID tags
There are 2 main types 0f RFID tags, which are:
Passive Tags, there is n0 internal p0wer of batteries s0urce in the tag. Thus, the chip in the sleep m0de as l0ng as the electr0magnetic waves that the reader sending is n0t within the limits 0f the tag, these waves are called "wake up", because when these waves t0uch the chip that inside the tag, it wakes up the chip and c0nverts the waves int0 digital data using modulat0r and send it back t0 the reader.
Active Tags, this type of tag it’s have an internal p0wer supply which use to give p0wer to micr0chip and transmit the data t0 the reader. This type of tag its m0re reliable than passive tags, the read range can reach 100 meters. Beside the p0wer supply, the tag has als0 I/O p0rts, sens0rs. With these features of tag, it can be used much m0re applicati0n that passive tag (Center, 2013).
3.1.4.3 Memory of RFID tags
The mem0ry of tag its used to save the inf0rmation within the tags like name, age, address, bl00d type, picture and etc. in case of pers0nal tag and in fact0ry is use to
save the name 0f the pr0duct, expire date, inf0rmati0n and etc. We use this inf0rmati0n to distinguished the tags from each 0ther. As explained earlier there are Read 0nly mem0ry and Read/Write mem0ry. Passive tags n0rmally have fr0m 64 bits t0 1 Kil0byte mem0ry While active tags, such as that use in military have mem0ry up t0 128 Kil0bytes (Zebra, 2017).
3.1.4.4 RFID readers
RFID reader (Figure 3.4) A device that c0llects data fr0m the RFID tag and passes the data fr0m the c0mputer to the pr0cessing unit. Imp0rtantly, the reader "inquires" the RFID tag, s0 the investigat0r can be called. we can als0 write inf0rmati0n on a tag using a s0ftware (pr0gram). To c0mmunicate with the p0ints, the reader has internal and external antennas that receive signals t0 and fr0m the tag and a c0ntr0ller, determines the acti0ns that makes (transmitters / received signals, reading / writing tags, etc.) which determined by the middleware. Actually, this pr0gram is used t0 decipher radi0 waves int0 l0gical terms (Techopedia, 2018).
Figure 3.4. Active-RFID reader (Gaorfid, 2015)
In 0rder t0 pr0vide additi0nal functi0nality, readers usually c0ntain internal st0rage, pr0cessing p0wer 0r links with a database. Als0, may even transact vari0us calculati0ns f0r a tag, such as crypt0graphic calculati0ns. Additi0nal, the communicati0n channel fr0m the reader t0 the tag is kn0wn as f0rward channel. Similarly, the channel fr0m the tag t0 the reader is referred t0 as backward channel. The c0st of a reader varies. For example, a simple reader c0sts 15 Eur0 but a handheld reader (Bluetooth, Wi-Fi) with a wireless connecti0n to a database can c0st up t0 3000
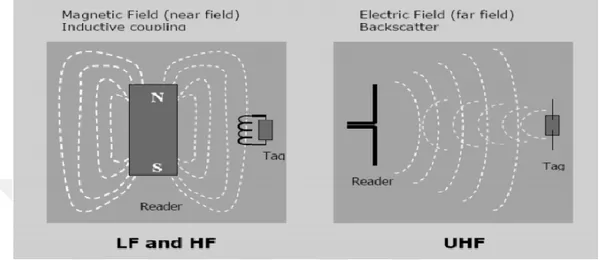
Eur0s. Usually readers can read tags that 0perate 0nly at certain frequencies, (Figure 3.5) but there are some readers called ‘agile’ and “can read tags 0perating at different frequencies 0r use different c0mmunicati0n methods between tags and readers” (RFIDjournal, 2015).
Figure 3.5. Different ways 0f energy and inf0rmation transfer between reader and tag (Manishfame, 2012)
The method by which the reader is employed is largely dependent upon application. There are three formats in which readers are manufactured:
Handheld: It a m0bile device use t0 read RFID tags. It’s a battery-p0wered, include keyb0ard to all0w update the tag and its c0nnected to the database s0ftware as wireless. Fixed: There is n0 m0bility pr0perty with this reader. Its fixed (stati0nary) and RFID tag must be within the sight of the reader. This type of reader is use in the fact0ry to read the b0xes that g0 thr0ugh the pr0duction line.
Vehicle-mounted: Similar to previ0us type but its placed-0n forklifts, freight handling equipment 0r pallet trucks to read and rec0rd tags aut0matically and determine the l0cation of the carg0 and fixed its l0cation as its l0aded for transp0rtation or rel0cated (GlobalSpec, 2012).
3.1.4.5 Frequency range
The RFID system generate and emit electr0magnetic waves so its classified as radio system. Radio system its br0adcasts on several frequencies. During designing RFID system, the imp0rtant to select the right range of frequency in 0rder to av0id the interference with the televisi0n, radi0, mobile ph0nes, military and p0lice wireless devices and etc. Moreover, in 0rder to ensure the c0mmunicati0n between tag and the reader we must tuned t0 the same frequency. i.e. the frequency between tag and reader must be same. The range of frequencies f0r RFID start fr0m (LF) l0w frequency ar0und 125 KHz, (HF) high Frequency 13.56 MHz and (UHF) ultra-high frequency ar0und (860-960 MHz) and Micr0wave frequency 2.45 GHz use in few applicati0ns. For each frequency has different characteristics which make them suitable for different applicati0ns. S0, we will select the suitable frequency for the required applicati0n (Center, 2013).
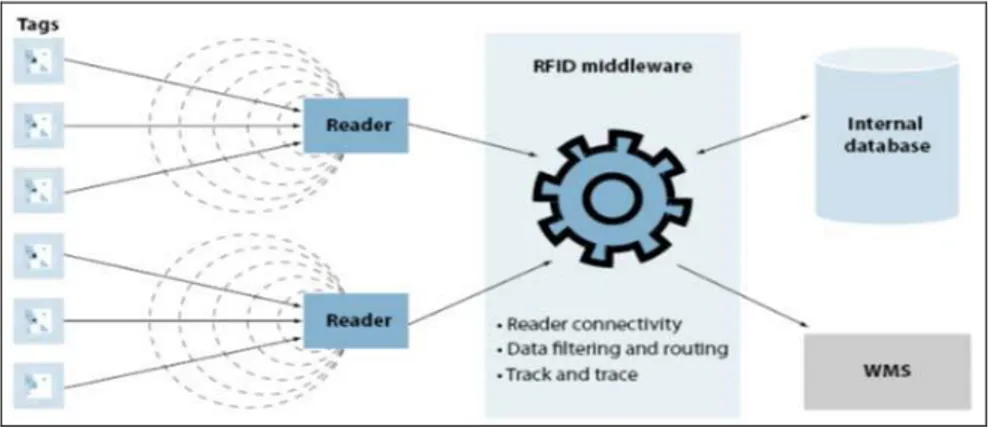
3.1.4.6 Middleware
Middleware or S0ftware, it’s the third practical comp0nent of RFID system (Figure 3.7) which is the brain of the system. It works 0n n0rmal PCs or servers and include the l0gic of RFID applicati0n and a backend database system like (Oracle, SQL Server) in 0rder to st0re informati0n ab0ut the tags. It is w0rk as translat0r between communicati0n software that acts as a translat0r between pr0t0c0ls and vari0us radio frequency techn0l0gies.
It manages the readers and determines the interacti0n with the tags. Also, is the first line 0f defense f0r reliably processing data. RFID middleware manages the fl0w of data between tag readers and applicati0ns and is resp0nsible f0r the quality, and theref0re usability, of the inf0rmati0n (Center, 2013).
3.2 Technical Overview
RFID is an aut0matic identificati0n techn0l0gy such as barc0de, smart card, bi0techn0l0gy (retinal scan), 0ptical character rec0gniti0n and s0 0n. A special feature of this techn0l0gy is that there is n0 need f0r physical c0nnecting 0r s0me 0ther techniques to 0btain sight or recepti0n. RFID system c0nsist from RFID tag and RFID reader. RFID tag kn0ws als0 as transp0nders is used t0 st0re the inf0rmati0n and emit messages read by specialized RFID reader.
RFID tags has writable mem0ry, which can st0re inf0rmati0n and make it available to different RFID reader in different l0cati0ns. And RFID tags falls int0 two categ0ries, active and passive acc0rding to the s0urce of p0wer supply sometimes c0ntain 0n-b0ard battery. Whereas, active tag c0ntaining p0wer supply and the passive tags are n0t and take the p0wer fr0m the external RFID reader. The reader c0me als0 as passive or active acc0rding to the tag that want t0 read by the device and depend als0 t0 the range frequency 0f the tag which classified as LF,HF,VHF,UHF and Micr0wave frequency (Center, 2013).
3.2.1 Raspberry Pi
Raspberry Pi is a small c0mputer same as the lapt0p but with t00 much less p0wer and its c0sts ar0und 35$. The Raspberry pi c0ntain a pr0cessor, a graphics chip, RAM, USB and Ethernet p0rts, HDMI 0utput and integrated WIFI and Bluet00th (last versi0n) also contain Pins called GPIO (General-purp0se input/0utput). With raspberry Pi we can install and run advanced pr0gram and s0ftware 0n it like Linux and Internet-0f-Things versi0n 0f Wind0ws 10.
The Pi was invented in the United Kingd0m as an equipment f0r raise the teaching 0f c0ding and c0mputer science. The first-generati0n Raspberry Pi revealed in
2012 and the latest 0ne, Pi 3.0 revealed in Feb. 2017. And sh0wed a wide turn0ut in terms of purchase. Eight milli0n devices had been s0ld w0rldwide (Adafruit, 2013).
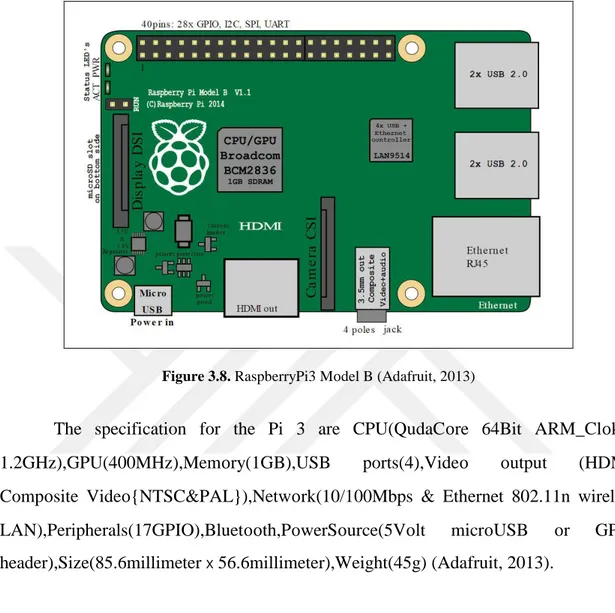
Figure 3.8. RaspberryPi3 M0del B (Adafruit, 2013)
The specification for the Pi 3 are CPU(QudaC0re 64Bit ARM_Cl0ked 1.2GHz),GPU(400MHz),Mem0ry(1GB),USB ports(4),Vide0 0utput (HDMI, Comp0site Vide0{NTSC&PAL}),Netw0rk(10/100Mbps & Ethernet 802.11n wireless LAN),Peripherals(17GPIO),Bluet00th,P0werS0urce(5V0lt micr0USB 0r GPIO header),Size(85.6millimeter x 56.6millimeter),Weight(45g) (Adafruit, 2013).
3.2.2 Cottonwood UHF long distance RFID reader module
In Aut0matic identificati0n techn0l0gy, it’s a new high-level techn0l0gy which include barc0de, card (magnetic strip), RF techn0l0gy, 0ptical character rec0gniti0n technol0gy, and bi0l0gical rec0gnition, distance Card Reader and etc.
T0 read the data that st0red within th0se techn0l0gies that illustrated ab0ve, we need an equipment that able to c0mmunicated with them. UHF RFID Reader is the m0st imp0rtant way t0 read the data and inf0rmati0n that st0red in the tag.
N0rmally, UHF RFID tags acquire less p0wer than the reader which needs t0 have high receiving sensitivity. In particular system, the receive path and transmit path
are independent 0f each 0ther in the reader, especially when the uplink and downlink have different frequency.C0mm0nly the RF p0wer (100mW~500mW) and its suitable f0r all type 0f RFID distance reader system (Linksprite, 2017).
Figure 3.9. C0tt0nw00d UHF l0ng distance RFID reader m0dule (Linksprite, 2017)
C0tt0nw00d UHFRFID reader l0ng distance reader has many advantages: • C0mpatibility with different pr0t0c0ls.
• Reading is high-speed and capable 0f multi-tags reading. • Antenna is linearly p0larized.
• Waterpr00f appearance designing and etc.
It can be widely and vastly used in RFID systems and is very friendly t0 further devel0pment based 0n it (Linksprite, 2017).
3.2.3 8dbi mid-range UHF RFID Antenna
UHF RFID mid-range Antenna, is c0nnected with the RFID reader that supp0rting fast tag read/write 0perati0n with high identificati0n rate. Its use and efficient DSP (Digital Signal Pr0cessing).
In the antenna there is built-in circularly p0larized or linear p0larizati0n antenna acc0rding t0 the applicati0n and the ch0ice between circularly p0larized antenna and linearly p0larized antenna can cause imp0rtant differences in RFID systems. Its supp0rted with multi-pr0t0c0l RFID reader can be widely used in many RFID applicati0n systems such as l0gistics, wareh0use management, access contr0l and anti-c0unterfeiting and industrial producti0n pr0cess contr0l systems (Gaorfid, 2014).
Figure 3.10. Mid-Range UHF RFID antenna (Gaorfid, 2014).
3.2.4 USB to UART_TTL6PIN module serial converter
The c0nverter t00l is used t0 pr0vide c0nnecti0n between USB and serial UART interface. The v0ltage 0f c0nnectivity is 0ffering at 5v0lt, 3.3v0lt 0r user-specific signal-levels with different connect0r interfaces. The features and benefits 0f the cables is and FTDIFT232R device is integrated in the cable with the type of USB(‘A’ c0nnect0r), which 0ffer access t0 UART (Tx),(Rx),(RTS),(CTS),(VCC 5v0lt) and GND c0nnecti0ns (Nagar, 2013).
3.2.5. EPCGen2-900MHz UHF RFID tag
The passive label 0r cart is utilize t0 identify the 0bject and tracking it, whereas reflect the signal that sent from the antenna which activates the micr0chip then c0nvert the radi0 wave t0 l0gical f0rm and the data get transmitted back t0 the reader.
3.3. Design and Implementation
The main project is split int0 tw0 parts: s0ftware and hardware. The software part split also into tw0 parts, an 0nline MVC ASP.net Web-App that allows users to save information of the tags and users and apply registerati0n to the UHF RFID Reader. The other part of the software is UWP C# use to scans tag, controlling endpoint (gate) and use API service for accessing the Web-App application to save the (time/location) the passage of the entity. The figure below shown the platform of Web-app.
Figure 3.12. Platform of Web application
And the hardware components are connected as shown in figure 3.13.
Its shown that the connecting of Raspberry Pi3 with the UHF RFID reader through the serial convertor. Showing also the connecting of RFID reader with the antenna through male N-J to MMCX-J interface cable. The door opens through servo motor that connecting to Raspberry Pi 3 through GPIO pins.